Cyber crime, like any crime, has its motives; each malware has its own malicious profit. Spyware spies on you. Ransomware demands a ransom to decrypt your private digital data. Phishing Malware phishes for your username, password or account numbers. Installation-fraud achieves fake software installations. Ad fraud fraudulently represents online advertisement […]
Detecting DoubleLocker Ransomware
What is DoubleLocker? Security researchers at ESET discovered a new ransomware infecting Android phones called DoubleLocker. DoubleLocker is an exploit that encrypts data on the infected device and then changes the device PIN to a random number. Victims remain locked out of their device unless they pay a ransom to the hackers. DoubleLocker spreads […]
Detecting KRACK Man in the Middle Attacks
What is KRACK? KRACK (Key Reinstallation attaCKs, KRACKs) is a serious weakness in the WPA2 protocol. WPA2 secures all modern protected Wi-Fi networks including those used by smartphones. Attackers within physical range of a Wi-Fi network can exploit protocol weaknesses by using key reinstallation attacks. The attack works against all […]
Validating Machine Learning Detection of Mobile Malware with Zimperium’s z9
Zimperium’s core machine learning engine, z9, has a proven track record of detecting zero-day exploits. We recently announced an extension of the framework that detects previously unknown mobile malware. This extension is known as “z9 for Mobile Malware”, and was officially announced in September 2017. Internally, the code name has […]
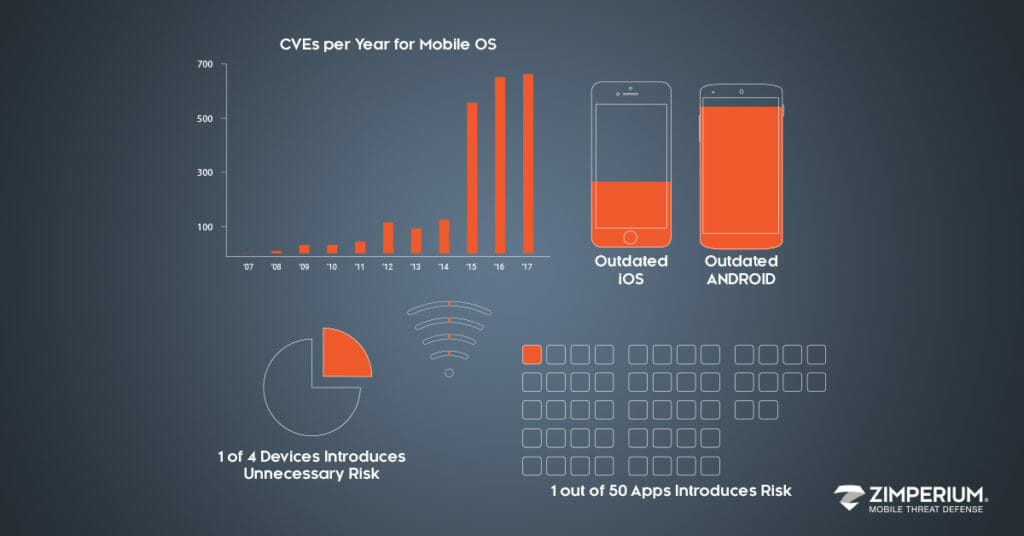
Mobile Threat Data Q2 2017
Zimperium is releasing its most recent summarized mobile threat data detected via our global enterprise customers. The data provides insight into what type of threats our customers are detecting by having the zIPS mobile threat defense app on corporate and BYO devices. zIPS enables companies to detect threats to mobile devices […]
Gartner Mobile Threat Defense and Enterprise Mobile Security Guide
“The signs are clear that mobile threats can no longer be ignored. Security and risk management leaders must familiarize themselves with mobile threat defense solutions and plan to gradually integrate them to mitigate mobile risks.”* *Gartner Market Guide for Mobile Threat Defense Solutions, Dionisio Zumerle, John Girard, 22 August 2017 […]
ziVA: Zimperium’s iOS Video Audio Kernel Exploit
Follow @doadam Following my previous post, I’m releasing ziVA: a fully chained iOS kernel exploit that (should) work on all the iOS devices running iOS 10.3.1 or earlier. The exploit itself consists of multiple vulnerabilities that were discovered all in the same module: AppleAVEDriver. The exploit will be covered in […]
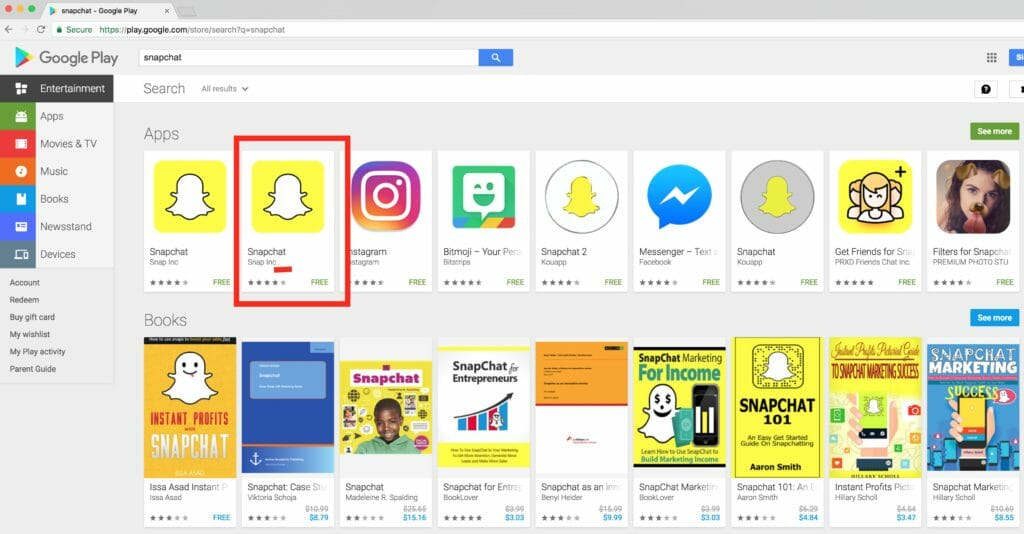
Fake Snapchat in Google Play Store
Zimperium discovered and reported a fake version of the popular Snapchat app in the official Google Play Store; At the time of our discovery, it was the second result when searching for “Snapchat”. The fake version of Snapchat app is using “Snap Inc .” as Company Name, with a ” […]
Zimperium zLabs iOS Security Advisories
As part of zLab’s platform research team, I’ve tried to investigate an area of the kernel that wasn’t thoroughly researched before. After digging into some of Apple’s closed-source kernel modules, one code chunk led to another and I’ve noticed a little-known module, which I’ve never seen before, called AppleAVE. AppleAVE was written neglecting basic security […]
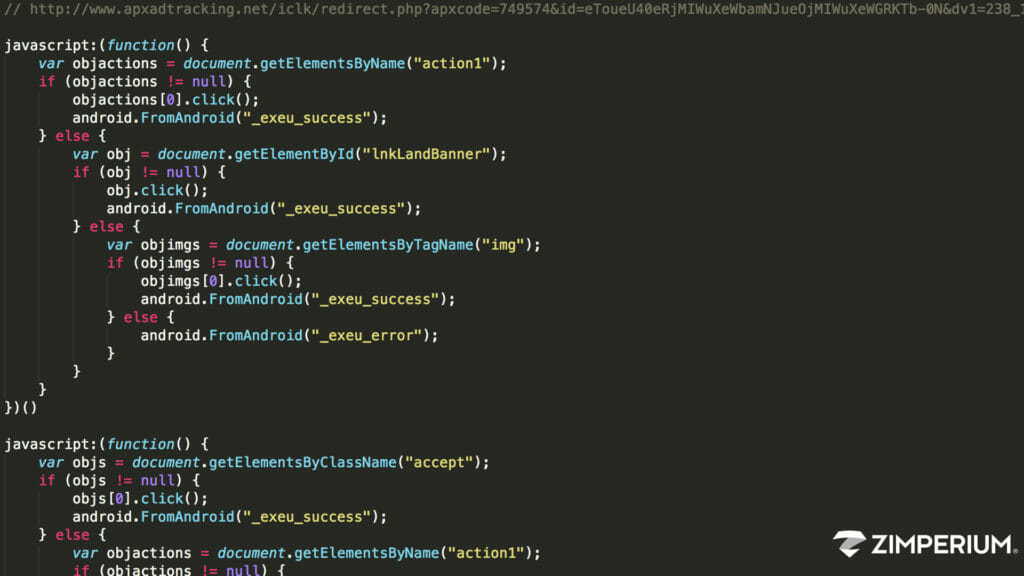
Threat Research: zTorg Trojan Variations
This Threat Research is about two variations of the zTorg mobile trojan recently discovered in Google Play by Kaspersky researcher, Roman Unucheck. In his blog post, Unucheck described the two variations as “Magic browser” and “Noise Detector”. According to Unucheck, “Magic browser” was uploaded to Google Play on May 15, 2017 and was […]
Mobile Security Updates
Recent Posts
- What Good Mobile App Security Visibility Looks Like: Discover What Lurks Within Your Enterprise’s Mobile Ecosystem
- Zimperium Positioned as the Leader in the 2024 SPARK MatrixTM for In-App Protection by Quadrant Knowledge Solutions
- Understanding IRAP: Australia’s Commitment to Upholding Best-in-Class Security Standards