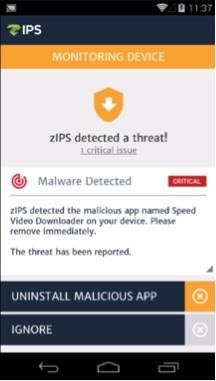
Several researchers have reported on the discovery of Hummer Trojan, as one calls it, or HummingBad as another calls it. Another said it was also known as Shedun. Zimperium’s customers are safe from this recently discussed threat even before these threats were published. The attack was detected through our z9 […]
Stagefright: One Year Later
It’s been exactly one year since Joshua J. Drake, our zLabs VP of Platform Research and Exploitation, disclosed Stagefright — one of the worst Android vulnerabilities to date. Stagefright impacted nearly 1 billion Android devices total, and up to 850 million devices remain vulnerable as of March 2016. Stagefright gives […]
Zimperium Applauds Google’s Rapid Response to Unpatched Kernel Exploit
On March 15th, Zimperium’s zIPS Mobile Threat Protection solution identified a zero-day mobile attack and its zLabs research team immediately reported the exploit to the Android Security Team. The reported attack is delivered via a publicly-available rooting application, KingRoot, using an unpatched local elevation of privilege vulnerability in the kernel reported […]
Reflecting on Stagefright Patches
42.84% of Android devices tested are vulnerable to CVE-2015-3864. Although Google issued an update to the Hangout app that disabled automatic processing of media files, we know that CVE-2015-3864 can be exploited remotely and reliably via the browser. The number of Android devices is estimated to be between 1.4 and […]
Triada Gets Tripped by Zimperium’s z9 Engine
Triada, a modular, stealthy and persistent Trojan targeting Android devices, was recently seen in the wild and reported on March 3, 2016. It, like so many others that we see daily, actively uses root privileges and operates silently to take over a device. Triada is primarily propagated through malicious applications […]
Experts Found a Unicorn in the Heart of Android
By:Zuk Avraham Follow Zuk Avraham (@ihackbanme)Joshua Drake Follow Joshua Drake (@jduck)Nikias Bassen Follow Nikias Bassen (@pimskeks) UPDATE: Zimperium’s Mobile Threat Protection customers are safe from this threat, even without updating the device to the latest Android version. Companies that have reasons to believe that they are under active Stagefright attacks, should contact […]
What Verizon Missed in the Latest Threat Report
By: Zuk Avraham, Joshua Drake, Yaniv Karta, Jimmy Shah (To download the detailed report, click here) Recently, Verizon published a report that says that malware on mobile is not an issue. We strongly suggest Verizon and other enterprises not underestimate the scale of one percent. The sheer number of mobile […]
DoubleDirect – Zimperium Discovers Full-Duplex ICMP Redirect Attacks in the Wild
By: Esteban Pellegrino, Zuk Avraham, Patrick Murray and Rachel Ackerly. Zimperium Mobile Security Labs have investigated during the last year a dangerous type of attack technique in the wild being exploited by attackers. Aptly named “DoubleDirect,” this attack is a type of “Man-in-the-Middle” attack (MITM) enabling an attacker to redirect […]
2015 Mobile Security Predictions – Mobile Attacks Move Mainstream
As 2014 inches to an end, Zimperium Mobile Security Labs researchers are actively preparing to stay one step ahead of attackers in the ever changing mobile security threat landscape. Due to the growing mobile device market, and the recent wave of attacks like Shellshock, Poodle, WireLurker and DoubleDirect, the Zimperium […]
Detection of TowelRoot & Exploits of CVE-2014-3153
Today we had the opportunity to see the engine of zIPS our Mobile IPS in action on a newly published vulnerability. As a reminder, we prefer complex problems, hence security on mobile devices is where we can think of out of the box ideas to solve security problems while […]
Mobile Security Updates
Recent Posts
- What Good Mobile App Security Visibility Looks Like: Discover What Lurks Within Your Enterprise’s Mobile Ecosystem
- Zimperium Positioned as the Leader in the 2024 SPARK MatrixTM for In-App Protection by Quadrant Knowledge Solutions
- Understanding IRAP: Australia’s Commitment to Upholding Best-in-Class Security Standards