Yesterday reports surfaced about China potentially using malware targeted at iPhone users to spy on Hong Kong protesters. Is it possible that a nation-state attack on an iOS device would be so bold as to use the words ODAY in its attack? Possibly… But what’s more important here is not the accuracy of the attack but rather how easy it is to compromise a mobile device and jeopardize your sensitive applications and corporate IP.
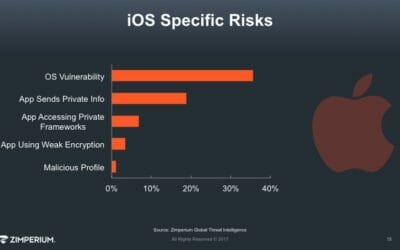
There is no debate, iOS devices are at risk for a host of mobile attacks. While hacking traditional computers has become increasingly difficult, mobile devices are still relatively unprotected and enable attackers to access internal networks easily. But they typically don’t make it that easy.
Let’s break this specific attack down:
1) Any iOS device at risk for this attack must already needed to be jailbroken (unlikely that a nation-state attack would limit its target to such a small bunch)
2) It’s not typical to see the words 0DAY in the attack code!
3) The attack was not aimed at protesters – but it was aimed at the media…(looks like it worked!)
Attacks on both iOS and Android devices are happening in the wild. They are simply going undetected. According to Claudio Guarnieri, an independent researcher from the University of Toronto’s Citizen Lab that investigates malware attacks, “There is no proof that this malware was ever distributed to anyone.” Jonathan Zdziarski, a forensic expert and security researcher, also weighed in on the discussion. “There’s no evidence that this malware has been used against Hong Kong protestors. And given that the malware needs a jailbroken iPhone to be installed, it’s unlikely that even if it were deployed, it would affect many people.”
Zimperium protected mobile devices are covered by this so called recent “threat” without any engine or software update.
So maybe this mobile attack didn’t impact its victims. It could have been distributed easily. Would you have been protected against such a simple mobile attack?
Organizations need to protect the whole mobile device for malicious behavior, not just scanning for apps, without reliance on signatures. Signatures are not immune to evasion techniques such as polymorphic engines, virtual machine awareness or runtime binary encryption and relying on them to provide enterprise class protection is risk. Enterprises need to deploy a solution that is designed to run efficiently on iOS and Android mobile devices that provides complete protection against both known and unknown threats. Enterprises should adopt solution that don’t employ app sandboxing or tunnel mobile traffic through the cloud, because it can compromise a user’s experience, violate privacy and drain the battery. Plus, complete solutions need to work in online and offline mode. Cloud solutions leave you vulnerable to attack while your device is unplugged.
For complete protection for both iOS and Android devices against, real-targeted attacks, contact us and we’ll help you to secure your fleet of mobile devices.