Mobile security is critical to supporting the modern workspace and Zero Trust
If there was one thing that has been said more than anything over the past year it’s that the corporate environment has changed. This distributed workforce shift we have experienced due to the COVID-19 pandemic has forced growth and change in so many areas of business that it can often be difficult to really keep up. But as organizations begin to really stabilize their operating procedures for the post-COVID lockdown, a new normal of enterprise security will emerge.
Recently, Phil Hochmuth, Program Vice President, Enterprise Mobility at IDC, presented his latest research on threats to mobile endpoints, its impact on the modern workforce, and how Zero Trust architecture is impacting the new, emerging normal for enterprises. While quite a bit of past research has focused on remote and in-office work models, Phil’s research dives into the modern workflows that have been adopted by individuals, introducing technology from outside the corporate umbrella, and the security implications of this change.
According to the research, a majority of enterprises going forward will be adopting some form of remote or hybrid work styles. In their survey asking professionals what the next 12 to 18 months looked like, IDC found that only 33% of workforces plan on being onsite only. The other 67% of workforces plan on either dedicated remote or hybrid work environments. But this latter approach to working introduces issues and challenges to most of the existing security technologies adopted by enterprises.
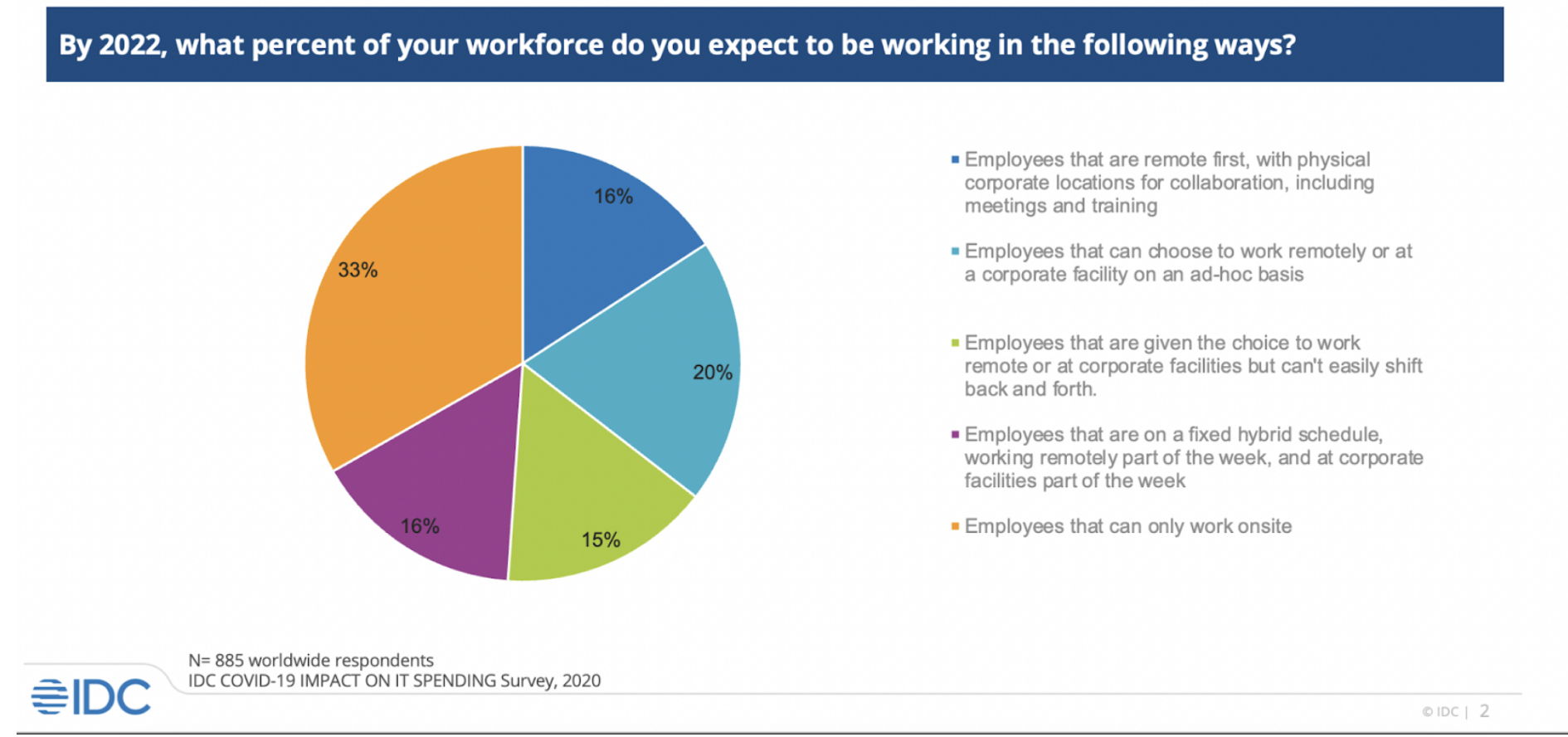 This big shift in the workforce and places employees work comes with a big caveat. Over the last 12 to 18 months, employees have changed not only where they do business, but the technology they are using.
This big shift in the workforce and places employees work comes with a big caveat. Over the last 12 to 18 months, employees have changed not only where they do business, but the technology they are using.
“Employees have collected a group of devices that are a mix of their own endpoints, corporate endpoints, personal devices and mobile devices that they’re starting to use to build out their workspace. And this new workspace is going to travel, whether the people have to go back to the office or if they continue to work from home or from a sort of a hybrid scenario.” – Phil Hochmuth
But as employees adopt these new workflows, they are also introducing risk through the increased usage of mobile endpoints on a daily basis. Security attacks like mobile phishing, malicious SMS, malicious networks and more are leaving enterprises and their data at risk. And enterprise IT and security teams are witnessing and responding to these threats on an increasing basis, highlighting the need for advanced security controls, like Zero Trust framework, to include mobile into its scope of coverage and protection.
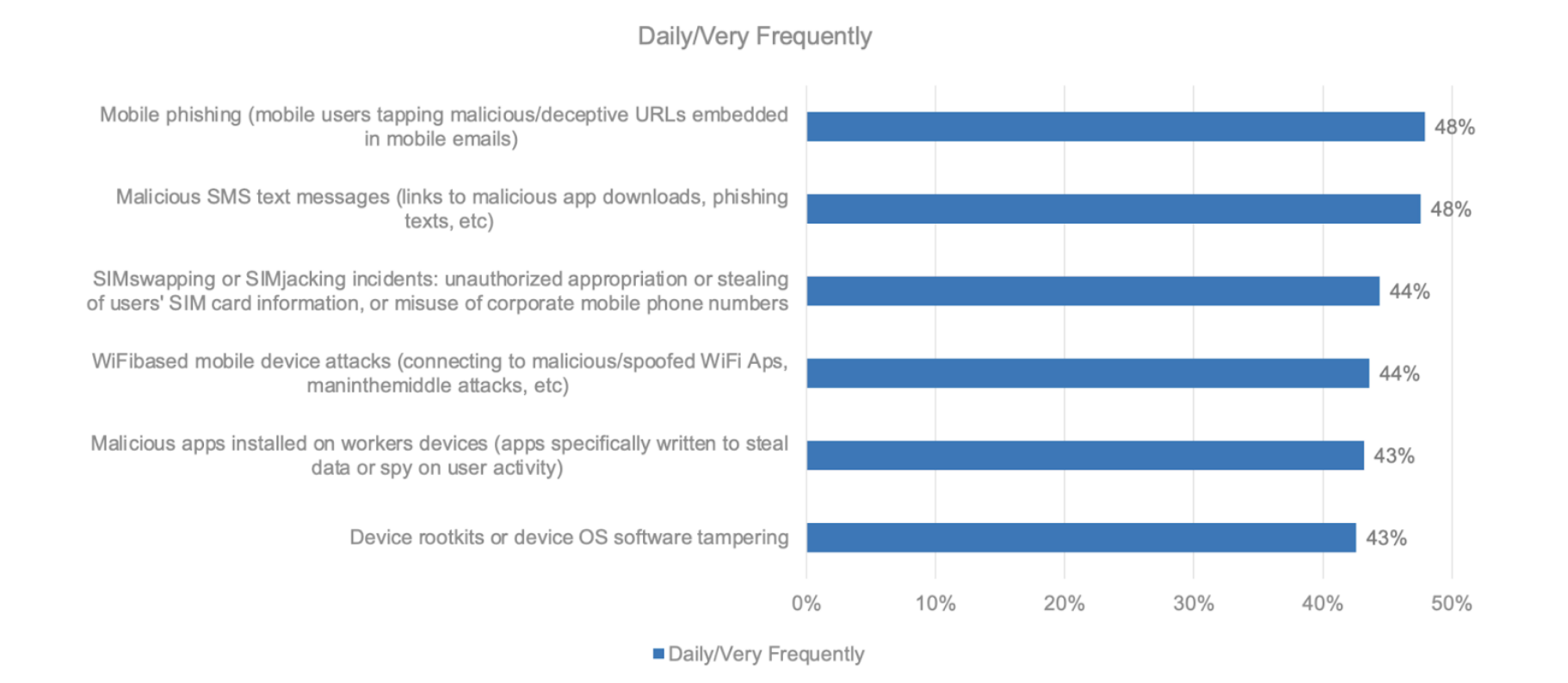 Enterprises are detecting more security incidents as employees are increasingly using mobile endpoints as part of their day-to-day activities. As attackers continue to look for the path of least resistance into corporate infrastructure, the devices with the lowest amount of security will often be the entry point. And no matter if the device is corporate owned or part of a strategic BYOD policy, it is necessary for security organizations to have the critical data and device attestation necessary to protect against advanced threats.
Enterprises are detecting more security incidents as employees are increasingly using mobile endpoints as part of their day-to-day activities. As attackers continue to look for the path of least resistance into corporate infrastructure, the devices with the lowest amount of security will often be the entry point. And no matter if the device is corporate owned or part of a strategic BYOD policy, it is necessary for security organizations to have the critical data and device attestation necessary to protect against advanced threats.
As security administrators deal with this increase in BYOD and corporate-owned mobile endpoints, they must adopt security architectures that assess trust and allocate access on a case-by-case basis. Unfortunately many services provided to mobile endpoints rely on legacy approaches to security and do not provide the necessary visibility or critical data to scale with these needs. And just as the traditional endpoint space evolved to address the common attack vectors with machine learning and critical data processing, so must mobile endpoints. This all becomes a foundational component of data security and trust for these highly used mobile devices.
By extending trust to mobile devices through advanced security architectures, enterprises and their employees can be safe even outside the confines of the office walls. But the only way to truly get to that point of trusting the untrusted is with Zero Trust architecture. And without mobile device attestation, Zero Trust architectures are left incomplete, leaving major gaps in corporate security.
Zero Trust for mobile endpoints relies on a shift in the focus of the security controls from location-based, in terms of on-premise networks, the extended controlled network, and those controlled devices, to an untrusted environment. Being able to push security to the user and the data and apps they’re using provide a perimeter of one around that individual and their productivity. This is a scalable solution that is able to move with the end-user and their data access needs as opposed to just having a sort of a broad umbrella of security.
“Windows has traditionally been the number one target for endpoints, but mobile is getting overlooked and it can be the personal nature of the mobile device that makes it most vulnerable.” – Phil Hochmuth
While enterprises of all sizes have been adopting both BYOD policies and Zero Trust architectures to support their security and productivity needs, the fact remains that not all endpoints are viewed as equal. According to Phil and IDC, security spending on mobile endpoints is on average less than 20% than what is spent on traditional endpoints. But with more valuable data being stored on mobile devices, along with critical work and workflows going through them, there is an increased risk due to the reliance and importance of mobile.
 This large gap in security spending also increases the risk of mobile use overall. The shift to remote and hybrid workforces has further complicated security on all endpoints. While traditional endpoints do receive a lot of security focus, cyber criminals are targeting all devices looking for the path of least resistance. While traditional and mobile endpoints are accessing the same critical data, the large gap in security adoption between the two is painting an easy target for malicious actors.
This large gap in security spending also increases the risk of mobile use overall. The shift to remote and hybrid workforces has further complicated security on all endpoints. While traditional endpoints do receive a lot of security focus, cyber criminals are targeting all devices looking for the path of least resistance. While traditional and mobile endpoints are accessing the same critical data, the large gap in security adoption between the two is painting an easy target for malicious actors.
Mobile endpoints are increasingly becoming one of the largest security blind spots for enterprises as many users and IT administrators assume these devices are secure or low risk. But the opposite is happening in enterprises; mobile endpoints are becoming a security risk due to the enterprise’s reliance on these devices for a critical component of the workspace.
Zero Trust architecture addresses the mobile threats by metering the level of access an employee needs based on their mobile risk posture, avoiding the umbrella security policies that have proven unscalable and inflexible in the intelligent workspace. And in order for enterprises to scale to the new normal, this intelligent workforce with a mix of workflows, endpoints, and locations of access, they must have complete visibility into all the endpoints connected to their data and make smart, persistent decisions based on the telemetry provided.
About Zimperium
Zimperium, the global leader in mobile security, offers the only real-time, on-device, machine learning-based protection against Android, iOS, and Chromebook threats. Powered by z9, Zimperium provides protection against device, network, phishing, and malicious app attacks. For more information or to schedule a demo, contact us today.




