Nicolás Chiaraviglio (@chiconara)
We recently blogged about attacks perpetrated at WiFi networks in Barcelona before and during the 2019 Mobile World Congress (MWC). We found an astonishing amount: estimating more than 7,000 threats in less than four days. Furthermore, 25 percent of those threats were detected in hotels, and of those, 70 percent were at 5 Star Hotels.
We now turn our attention to San Francisco and this week’s RSA, a conference dedicated to information security. Like MWC, the most important companies in the world are represented at RSA, with a total attendance of almost 50,000 attendees – – executives, salespeople and a who’s who of security experts. For hackers, this represents a treasure trove of targets to steal corporate and personal information.
…But there is not much to be concerned about here – – RSA attendees are obviously security-aware, right? Well…
Before we start, a reminder: the data we are showing is based only on phones using the Zimperium’s zIPS app, the world’s first on-device mobile intrusion prevention system app that provides comprehensive protection for iOS and Android devices against mobile network, device, phishing and application cyber attacks.
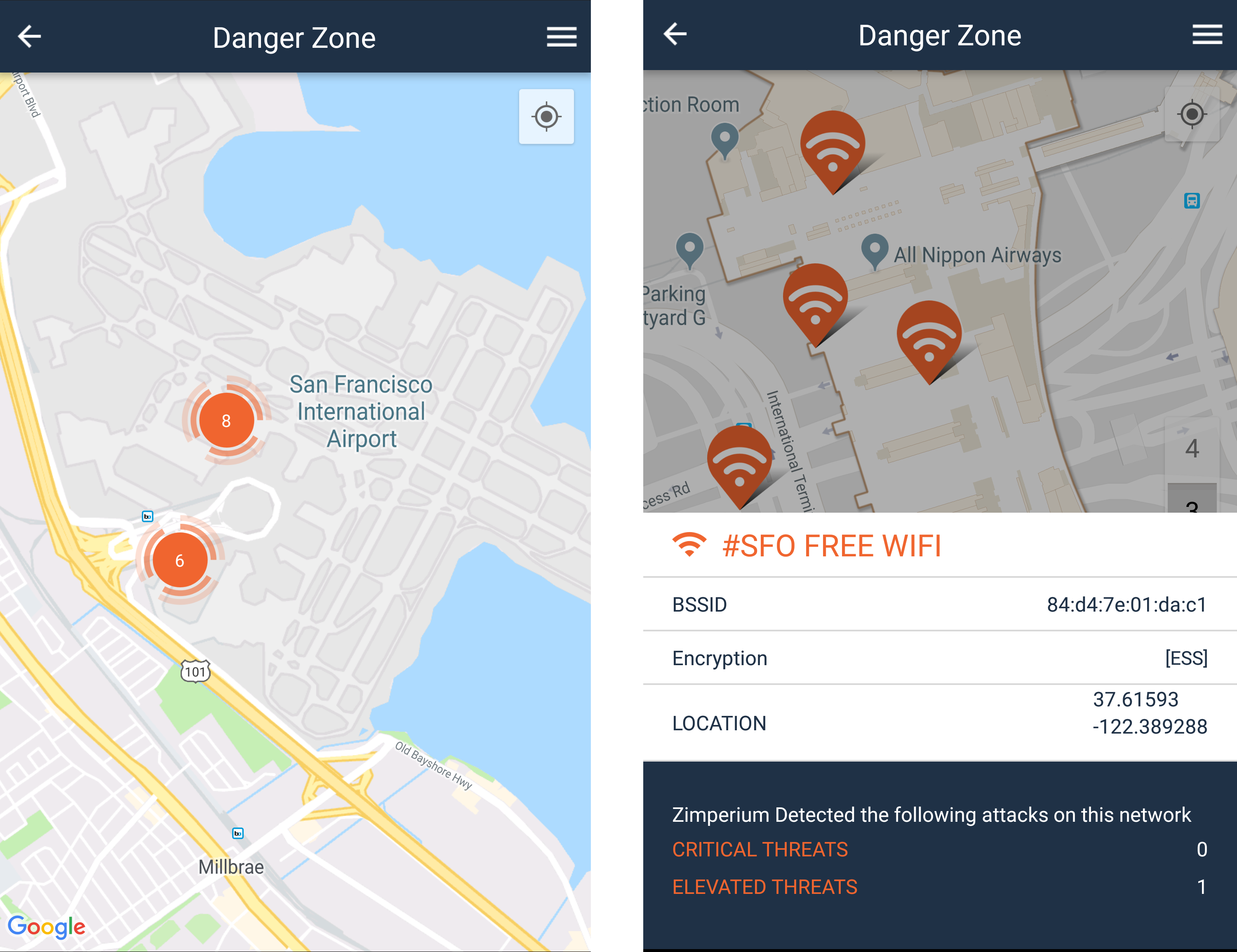
In Barcelona, we found the airport was a popular place to perform attacks. Well, it is no different at SFO Airport:
Everyday, Zimperium detects six hundred millions threat events. We process the most relevant network threats viewable in Danger Zone – a real time map that warns and prevents you from connecting to malicious WiFi networks. Danger Zone shows 14 elevated or critical events registered in the airport. Furthermore, those threats were over the airport free WiFi network (or someone pretending to be it).
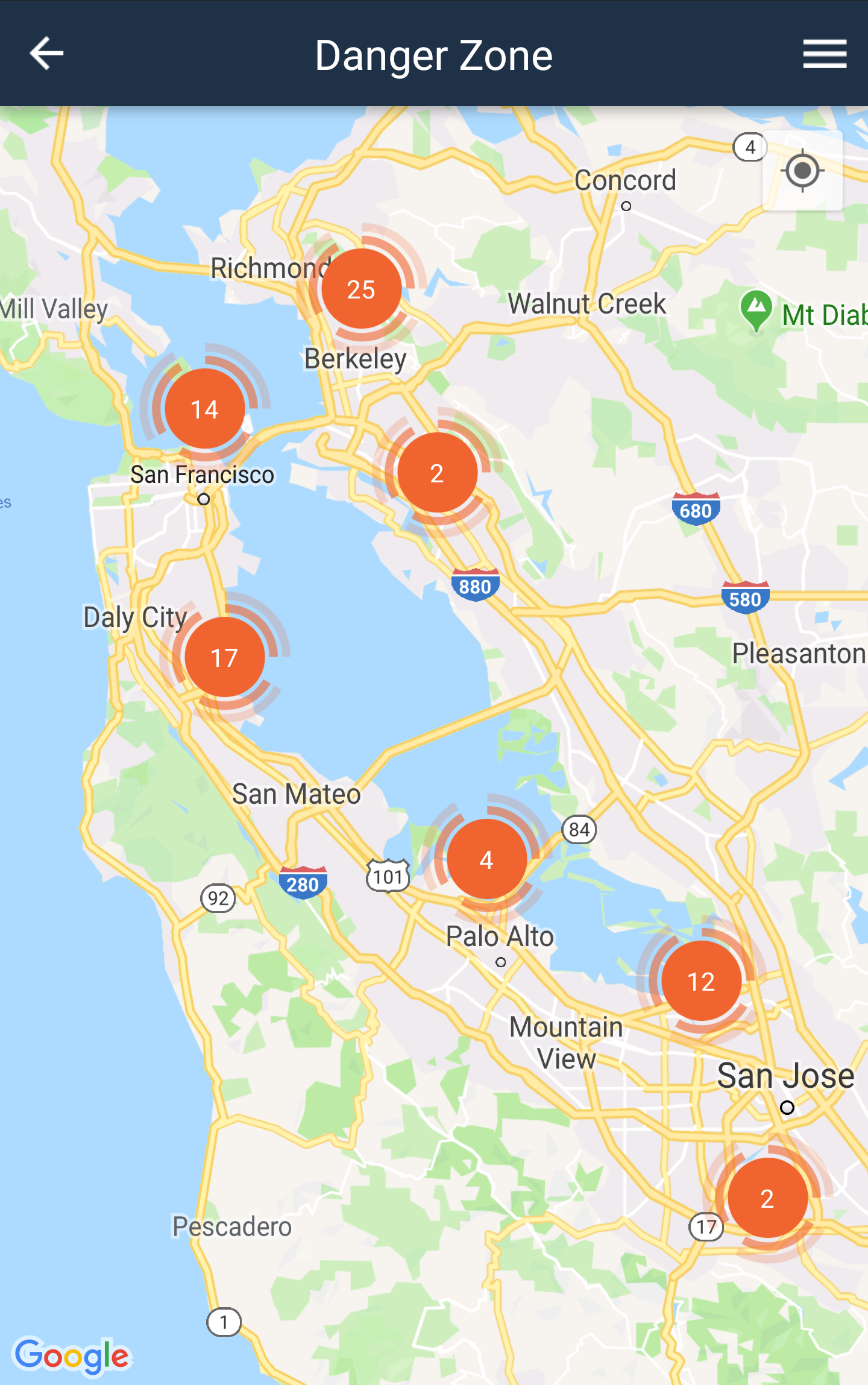
Let’s now zoom out to check how the Bay Area looks like from the Danger Zone perspective:
As we review the Bay Area, Danger Zone only show events with these criteria:
- The threat took place less than a year from the current date.
- The severity of the threat must be what we call Critical or Elevated. This means threats in which the attack type can compromise the device.
- Full GPS location must be available from the attacked device.
Let’s remove criterion two (severity) and create a new map with all the events we’ve detected at the airport.
Before we do, let’s clarify what constitutes a critical or elevated threat. If an attacker is performing a scan to discover devices in the network, we will warn the user about this, but it doesn’t represent a critical threat on its own.
Once the attacker knows about your device, he/she can perform a man-in-the-middle attack (routing all your traffic to his/her own device, thus being able to steal information). This will be considered a critical threat since personal information may be compromised. If a user is using zIPS, most attacks are prevented while the scan is taking place, but some attacks don’t start with one and we’ll get events with higher severity. So, let’s also add to the map the attacks prevented in an early stage.
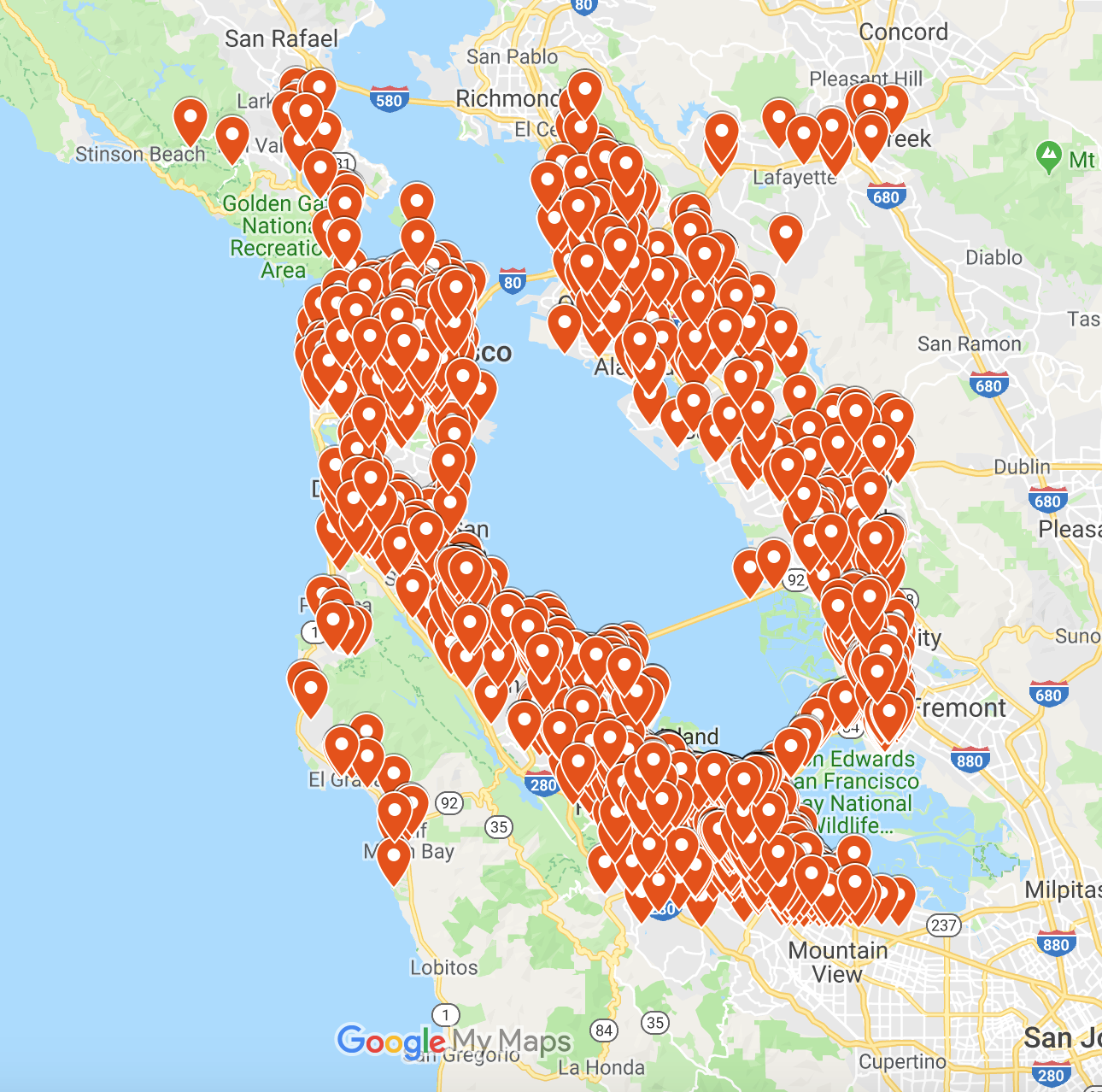
So the full event landscape of the Bay Area – and the airport – looks like this:
Due to the large number of registered events, we’ve only showed events with unique network names. Even doing this, the map is covered by the markers.
By zooming in, the number of markers is staggering:
As was the case in Barcelona, there is no place to hide.
Show me the venue!
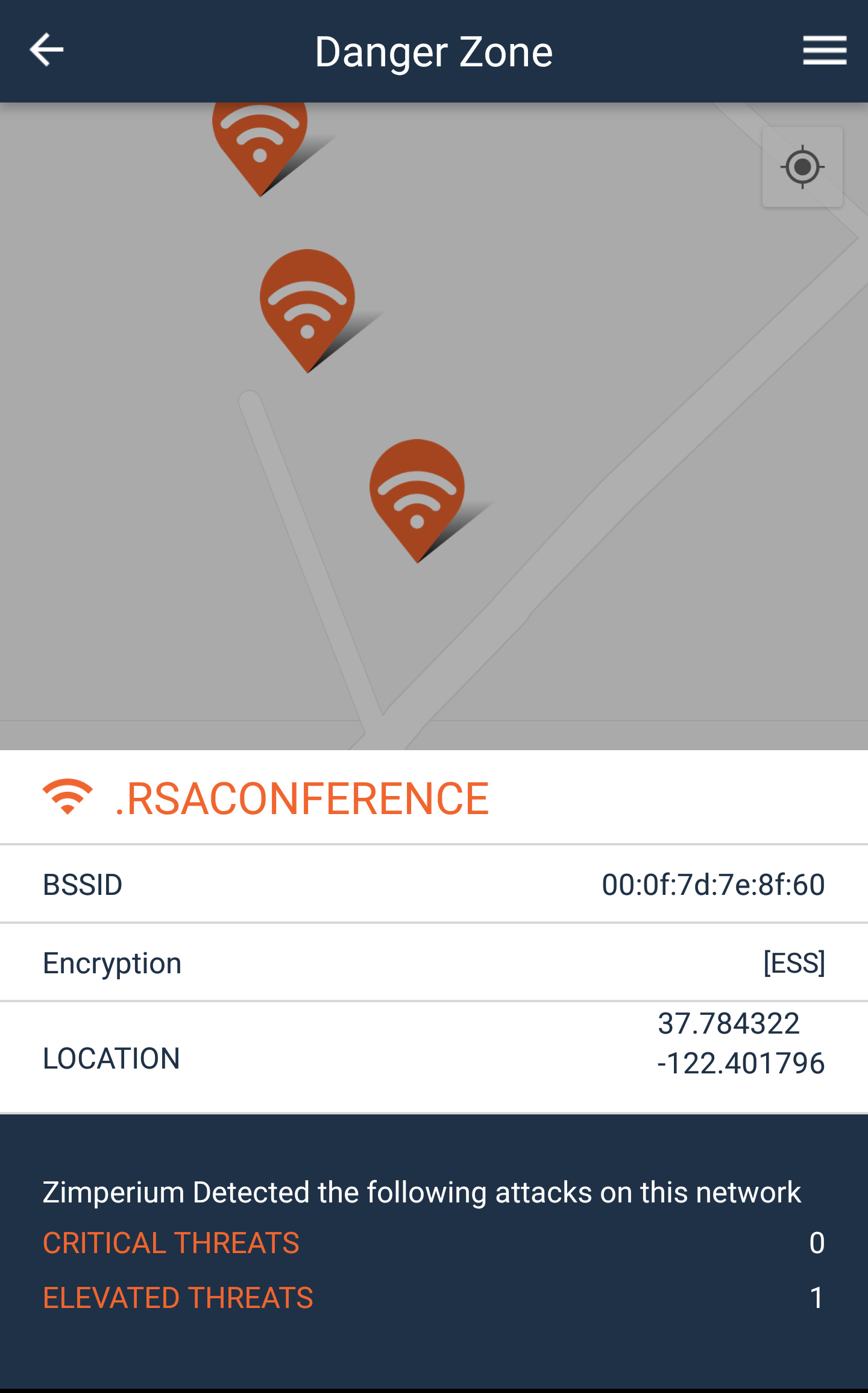
RSA is taking place at Moscone Center. If we check the surrounding area, we find this:
If you’ve read our latest post, you are not surprised to find the conference’s network among the attacked. Again, if we remove the severity criterion, the full landscape of attacks looks like this:
Some stats about the city
Checking the name of the networks we can learn a lot about the city and in which places most threats take place. What the San Francisco threat landscape is showing to us is:
- Total number of network events during the last year: 851,186 (1,998 per day)
- Events registered on networks with the word “hotel” in their SSID: 2,897 (almost 7 per day)
- Threats at RSA network: 486
- Unique attacked SSIDs: 5,860
Among these events, we find restaurants, coffee franchises, fast food restaurants, hotels, airport wifi, open city networks (like SFO-Public, SFO Free WIFI – and it’s 5G version-), museums, stores, big tech offices and the best discovered network: “the_rickest_rick_5G”.
If you’ve read our previous posts about WiFi security, you’ll notice that the number of detected events is much higher than in Barcelona. This is because the number of sensors we have in San Francisco is much bigger than in Barcelona (due to the number of Zimperium users).
If we only consider the attacks that took place from Saturday, March 2 to Tuesday, March 5 we find this:
- Total number of threats: 17,345 (3,854 per day)
- Threats at hotels: 39 (almost 10 per day)
- Unique attacked SSIDs: 637
- So far we haven’t detected events on the RSA network (good job RSA team)
If we compare the number of threats at hotels, we can see that during RSA, this number increases a 40 percent. Also, the total number of events in the city is 92 percent higher than the annual average. This difference can be explained by three factors: the increase in the number of devices with zIPS, the annual seasonality of attacks, and the events bringing a lot of people to town, such as RSA.
Temporal distribution of the events
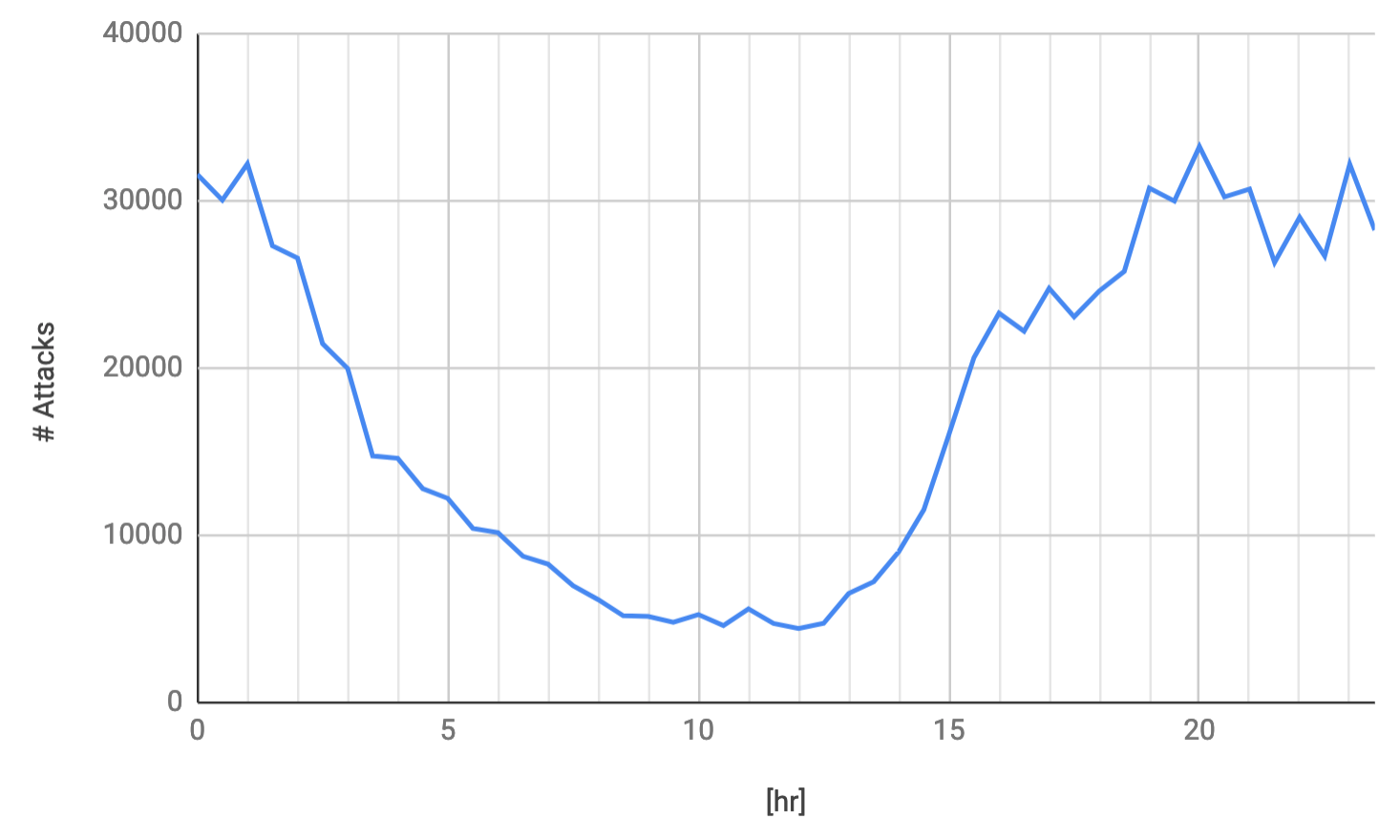
Since we have a lot of events, it makes sense to analyze the temporal distribution of them. We’ve analyzed the daily and annual distributions. The daily one looks like this:
We can see how hackers tend to be more active from 7 pm to 1 am, while the attacks diminish from 1 am to 12 pm. Yes, you are right… they sleep a lot!
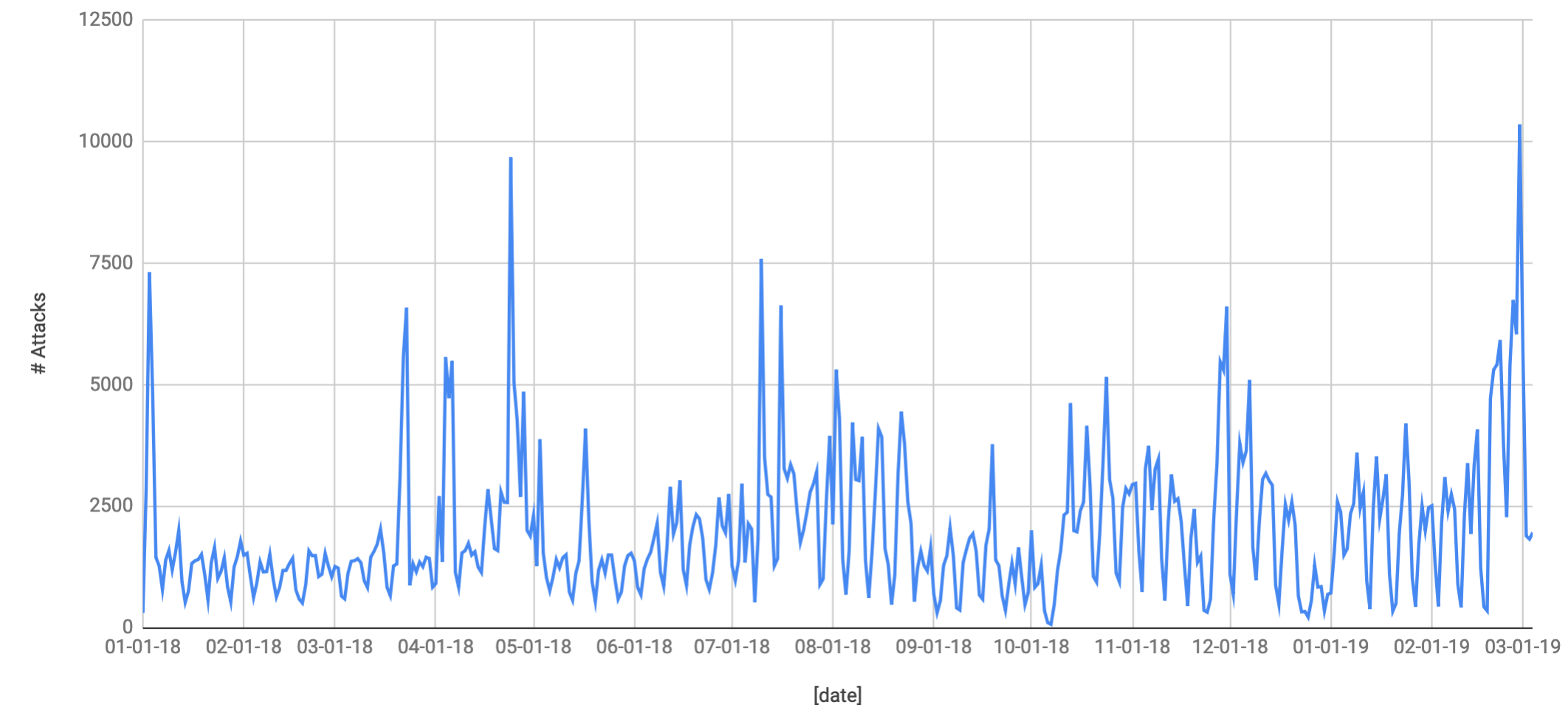
The annual distribution is:
The annual distribution of events show peaks that can be related with periods such as conferences, sports events, festivals, etc. Also, there is a tendency to detect more numbers of threats with time since the number of devices with zIPS installed is also increasing. From these charts we can find the days with the most and least number of attacks. In 2018, the day with most events was March 24, with 9,679 attacks. On the other hand, on October 7 “only” 68 events were registered.
Another interesting fact about the events is the ripple that can be observed in the chart. If you are thinking about days of the week, you are right again. Unsurprisingly, during the weekend the number of events is reduced drastically. The average number of threats by day of the week can be found in the following chart:
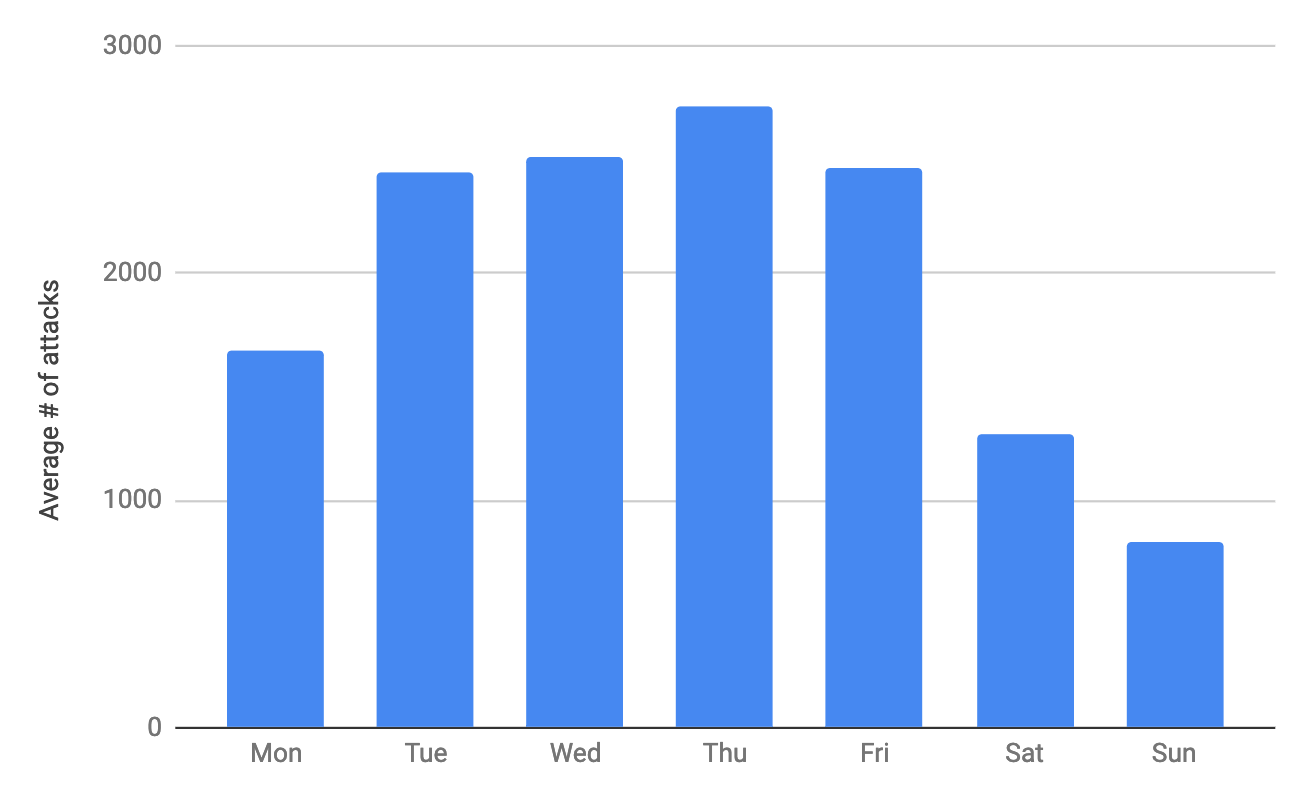 One possible reason for this behavior is during working days people tend to connect to more WiFi networks (when going for lunch, for example). In this case, corporations need to be aware of how important is to protect their workers in their everyday activities.
One possible reason for this behavior is during working days people tend to connect to more WiFi networks (when going for lunch, for example). In this case, corporations need to be aware of how important is to protect their workers in their everyday activities.
How can I avoid being attacked?
The best you can do to avoid being attacked is to avoid all possible connections. You cannot threaten what you cannot see. But let’s face it, we are online 24/7 and that’s not a realistic. So, what else can we do?
- Configure devices to not connect automatically to known networks. This can be done easily on iOS, but on Android it has to be done for each network. A workaround is to delete known networks periodically.
- Don’t connect to open WiFi networks or networks using weak encryption protocols.
- If you connect to these networks anyway, avoid activities involving credentials (email, social media, banks, etc). This won’t prevent hackers from seeing traffic, but no credentials can be accessed by sniffing the traffic (although hackers are still able to perform other kinds of attacks like directing the user to a malicious website in which the user can be tricked to install malicious apps, etc,.).
- Use a VPN which will encrypt traffic and show an attacker a nice set of nonsense characters. That said, VPNs will not protect against malware detection, anomalies in processes, phishing attacks, device compromises and malicious profiles.
If you want to know more about mobile security, visit us at RSA (booth N4410), go to our website: www.zimperium.com, or send us an email to sales@zimperium.com.