Millions of Android users have been impacted recently by malware masquerading as a card game called Durak, an IQ test and a history app.
The discovery was made by Avast security researcher, Flip Chytry.
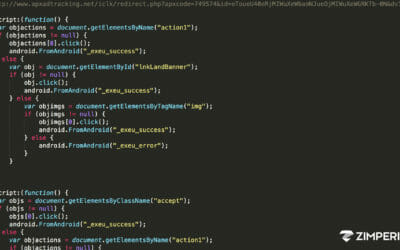
The malware contains fake ads that pop-up whenever an unsuspecting user unlocks their device. The ads warn users about fake issues – suggesting the device is out of date, contains pornography or even has been compromised. Victims are then encouraged to take further action, setting themselves up for even more risk. So how did these malicious apps make their way onto the Google Play store in the first place?
VP of Products at Zimperium, Patrick Murray, shared his insights with TechNewsWord yesterday. While the Zimperium Security Labs Team not yet evaluated the malware in question, we do suspect that Google Play did not find the malware during their app scanning process, since they rely mostly on static code analysis and the app in question may have used a “timebomb” method of waiting a period of time before downloading and executing the malware. This is a core vulnerability when it comes to apps. All apps have a server side component that it regularly communicates with long after the app has been “blessed” by the app store curators (in this case Google and Avast themselves). After receiving a good bill of health from the app store, the app wakes up and receives new malicious instructions from a third-party server, and delivers the payload to the device. This is why you cannot depend on “point in time” inspection for protecting you from malicious mobile apps. And this is also why enterprises must consider adding protection against malicious attacker as part of their BYOD strategy.
With the rise is BYOD programs, these types of threats pose an increasing risk to employees who utilize the same devices for work and play. Malware downloaded on the personal side of the device can easily compromise the enterprise network by stealing corporate credentials or simply bringing the compromised device back onto the network. Once a device has been compromised, and an elevation of privileges has occurred, the attacker basically has complete control of the device, and is free to harvest both personal and corporate information through a variety of means.
Businesses need to think about expanding their BYOD initiatives to go beyond simple management of devices and employ solutions on the device that prevent these types of cyberattacks, so that this type of malware doesn’t end up stealing valuable corporate data. One such way is to employ solutions that are continuously monitoring for threats on the device so that malware is caught whenever it is delivered, even if it tries to “lie and wait” for a period of time before detonation.
This is just another example of how static signature or app reputation based solutions are not equipped to handle today’s advanced mobile threats. You need a solution that can detect unknown threats by continuously running on the device rather than a simple check of a blacklist of known malicious apps.