Zimperium is releasing its most recent summarized mobile threat data detected via our global enterprise customers. The data provides insight into what type of threats our customers are detecting by having the zIPS mobile threat defense app on corporate and BYO devices. zIPS enables companies to detect threats to mobile devices in real-time, so attacks via mobile vectors stop at the device level and don’t advance beyond the targeted device.
Our customers detected hundreds of thousands of threats from April 1 through June 30, 2017, at the device, network or app levels. We also investigated a sample set of 50,000 iOS apps with z3A. The investigation uncovered security and privacy issues in the apps that are cause for concern for any enterprise.
- Device Threats and Risks – Threats to the device or OS, including unpatched vulnerabilities
- Network Threats – Threats delivered to the device via the cell network or Wi-Fi
- App Threats – Mobile malware, spyware, adware, or “leaky apps” on devices
Highlights and Key Findings in the report include:
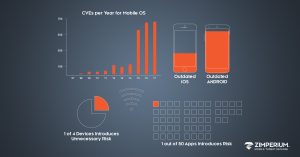
- In the first half of 2017, there were more CVEs for Android and iOS than all of 2016
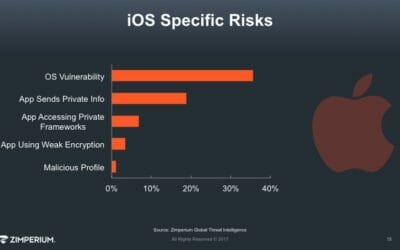
- 1 in 5 iOS devices is running outdated software
- Users installed unauthorized VPN apps to circumvent corporate compliance policies
- 80% of devices detected a MITM after detecting a scan
- 1 in 50 apps on enterprise devices have serious security or privacy abuse issues
The report contains high-level statistics aggregated from Zimperium customers around the world. Each enterprise customer operates its own mobile threat defense environment and independently manages compliance and remediation policies based on corporate procedures and preferences. Every environment contains detailed forensics on each threat and attack, enabling security teams to perform detailed analysis on which device was attacked, where it was attacked (if configured) and what processes were running on the device at the time of the attack.
Download the Zimperium Global Threat Report Q2 2017
Slides are available on Slideshare so you can share with your teams. If you would like us to provide a customized presentation to your team and answer questions about mobile security, contact us and we will provide you with information tailored to your needs.