
Affected Component: all iOS versions < 14.0 LSDIconCache
Latest Vulnerable Version: iOS 13.7
Vendor: Apple, Inc.
CVE: CVE-2020-9773
Disclosure Timeline
Bug discovered: December 1st, 2019
Vendor notified: December 17th, 2019
First patch attempt: March 24th, 2020
Final patch released: September 15th, 2020
Summary
A sandboxed application can circumvent updated iOS restrictions to enumerate installed applications on a device.
Impact
A malicious app may be able to track, access and enumerate the current device installed applications.
Background
Listing the installed application on a mobile device has created a lot of traction from analytics, and advertising brokers. One of the go-to approaches of identifying a mobile user is enumerating the installed applications and their application paths.
Optimizing ad exposure on multiple applications is a great concern for this market; that is why enumerating installed applications is a golden-key solution, as it allows 3rd parties to coordinate ad exposure and campaign managers to synchronize their effort among multiple applications.
Apple invests into mitigating privacy issues within its iOS/iPadOS operating systems. During the evolution of iOS we have witnessed an ongoing focus into mitigation of many privacy issues such as improving the user consent for GPS, calendar, contacts and photos usage, restricting Mac address enumeration, pairing with new hosts, installing profiles and more.
The Cat and Mouse Game
From a privacy point of view, enumerating the installed applications has a great impact on users’ privacy because it can easily be abused to characterize and tag the user and its profile. This is why – like in a cat and mouse game – Apple is actively removing any API allowing 3rd party and shady applications to list the installed applications, and vice versa, the adversaries are actively looking into new ways of circumventing these mitigations.
For example, over the evolution of iOS and its sandbox, several private API calls were blocked to mitigate enumeration of the installed applications, such as the private API call of [LSApplicationWorkspace defaultWorkspace] allInstalledApplications] which was patched as of iOS 11.0 and can be seen in this blog post (only in Chinese):
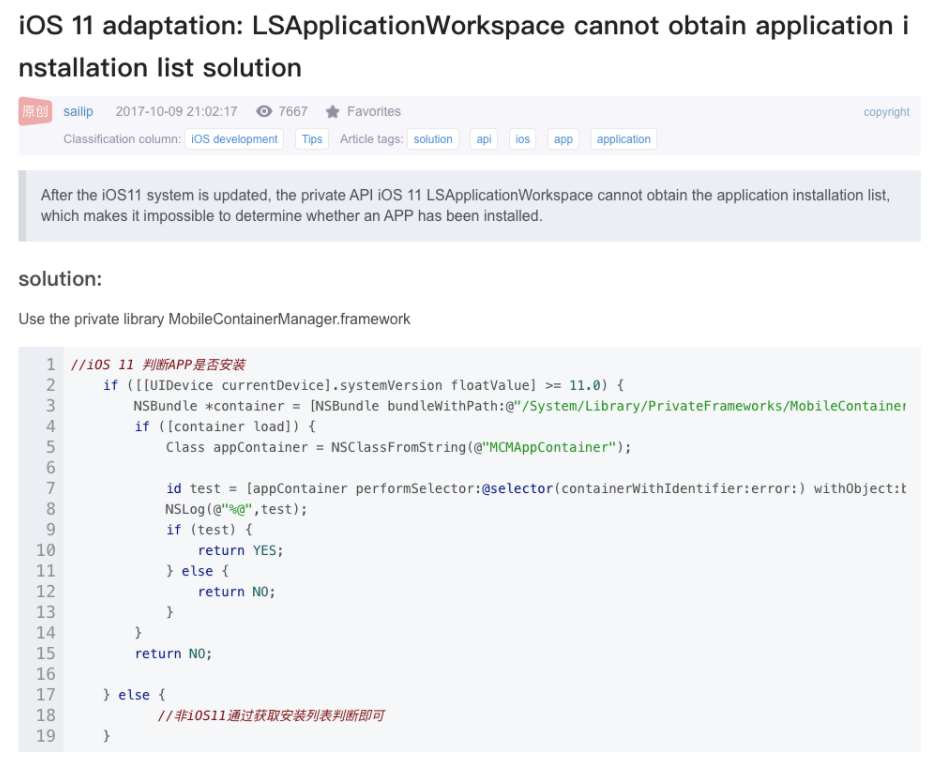
The bypass suggested in that post for enumerating the application lists on iOS 11, was to choose a different private framework (MobileContainerManager framework), and abuse the API of its MCMAppContiner class to do the same work.
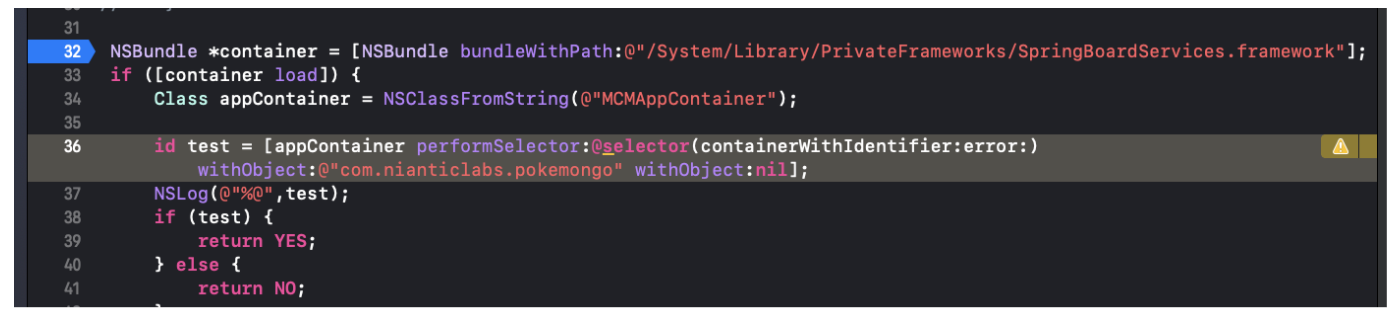
As an example, the following code snippet will use the new private API to check if the PokemonGo application is installed on the current device:
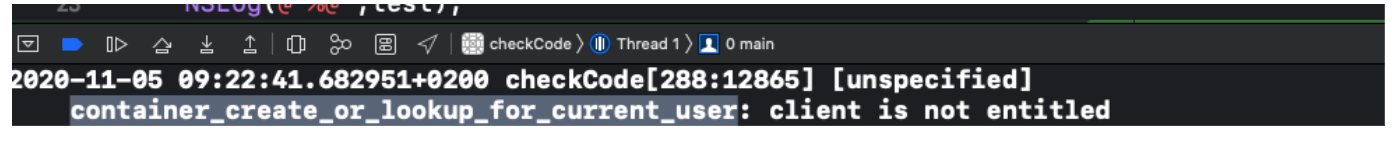
As can be viewed in the output window, this call was blocked by Apple on iOS 12.0 Beta by implementing a new mitigation in the form of an entitlement check.
The Icon Cache
Each application on the iOS/iPadOS ecosystem is represented by a unique icon. These icons are created by the application developer and are used to assist the user in identifying and interacting with the application on Apple’s various operating systems.
During the application installation process, the iOS/iPadOS operating system caches the application icon as a converted Apple format and uses that cache file to represent the application for the user.
The Vulnerability
All of the cached icons are stored in a persistent folder. The path to this folder is constant across every device and for every user. The folder was found to be globally accessible to read from within the sandbox; resulting in any application, on any device, reading the contents of the icon cache folder and processing the cached icon files. Hence, any application could enumerate the list of installed applications.
Technical Details
LSD is using a global read folder to store iOS icon cache files. Icon cache is stored in a BGRA32 proprietary format for Apple. Any application can bypass the sandbox and access this folder to enumerate these icons and impact iOS user privacy.
LSD Icon Cache Format
The Icon Cache Format used by LSD can be easily reversed, Below is an example of this header on iOS 13.3 Beta:

Storage
Icon cache storage resides at: /private/var/containers/Shared/SystemGroup/ systemgroup.com.apple.lsd.iconscache/Library/Caches/com.apple.IconsCache/ filesystem path.
Proof of Concept
On the latest beta iOS device, we have installed several applications such as shown in this image:

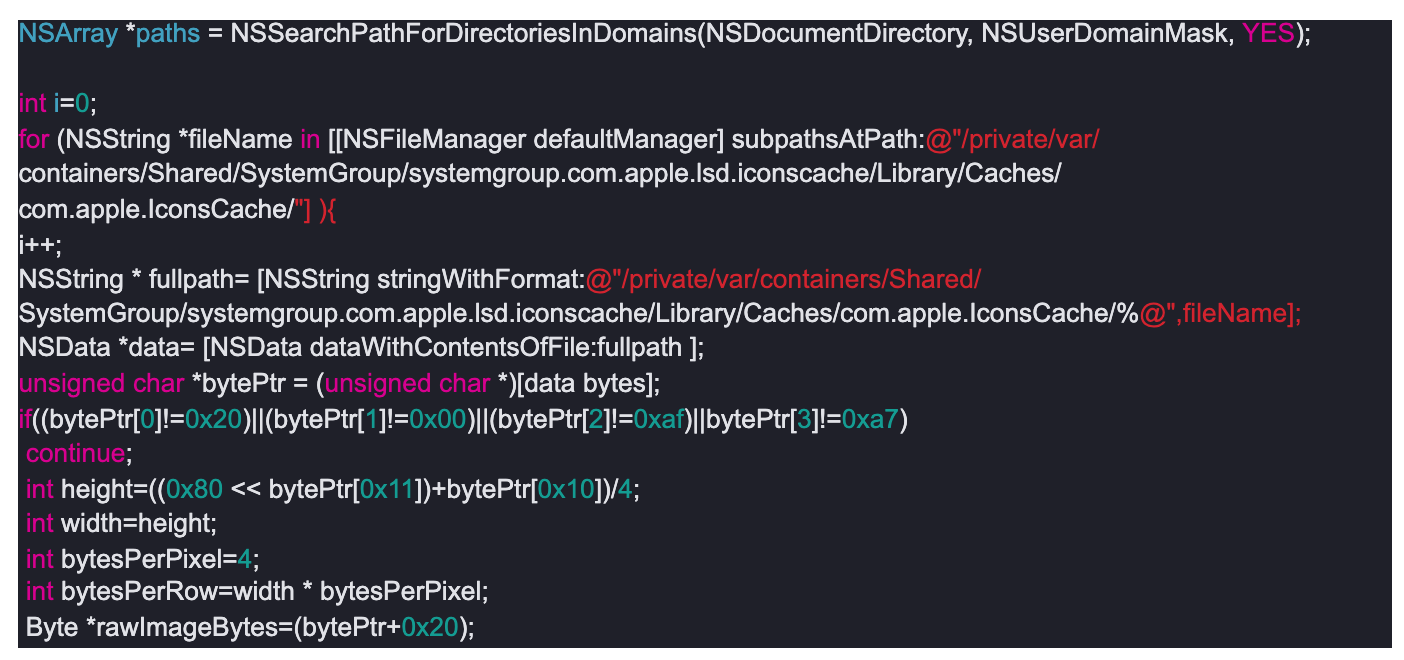
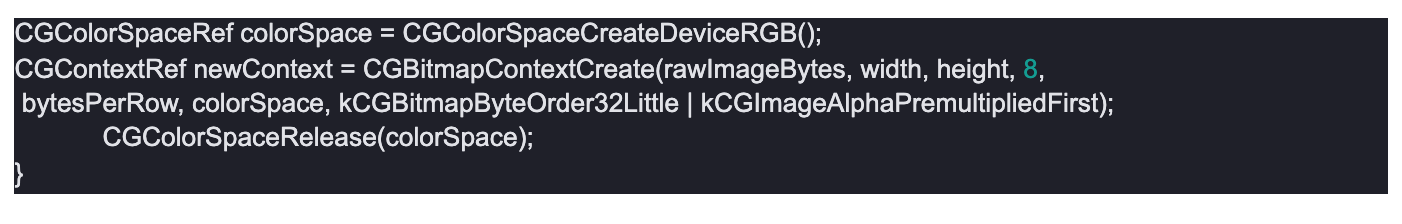
The attached proof of concept application demonstrates the vulnerability by enumerating every installed application on the device, and saving its icon in a general png format in its document folder. Relevant example logic follows:
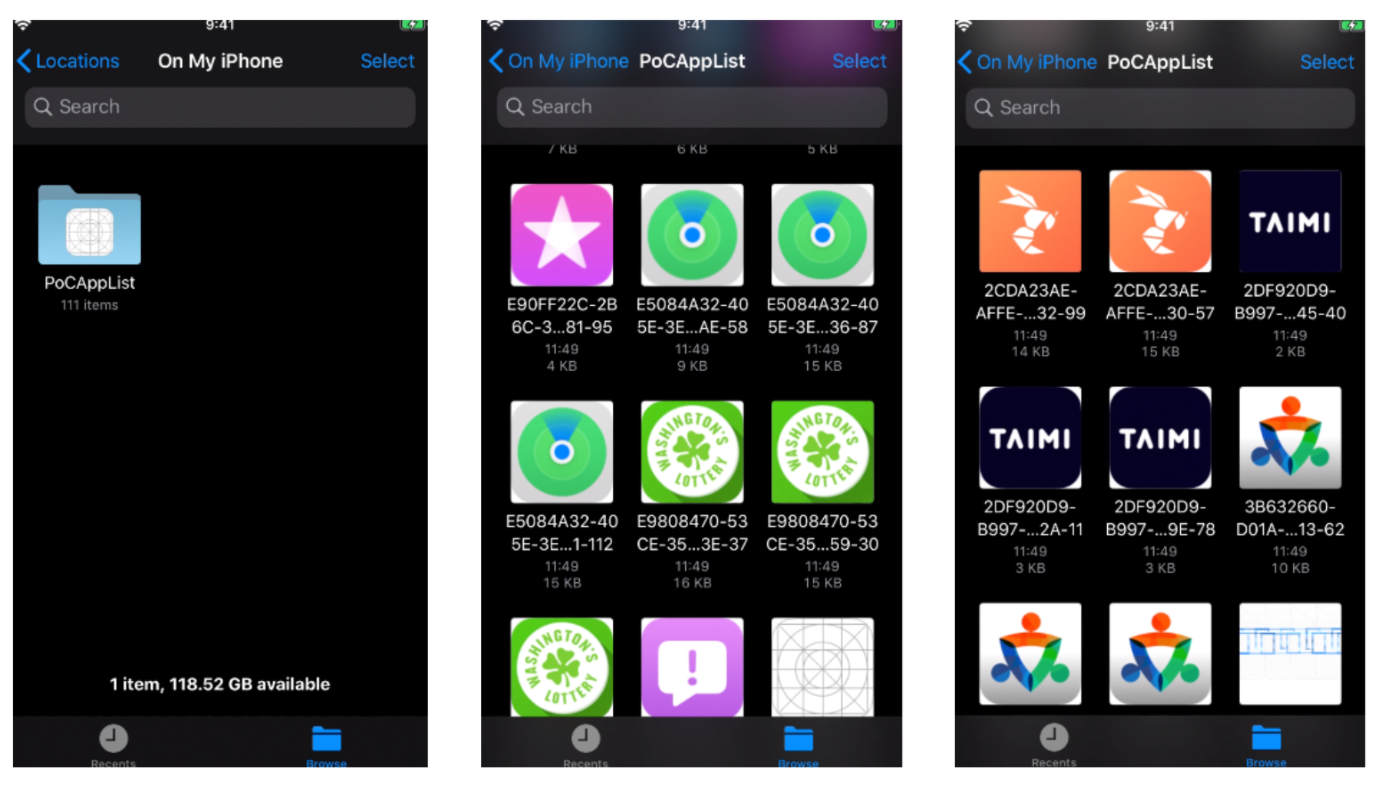
The icon can be viewed directly by using the files application on the PoCAppList folder, as shown below:
The Fix
Apple has patched this issue on iOS/iPadOS 14.0. We recommend users upgrade to the latest iOS version.


