In our previous blog post, we wrote about what’s planned for 2014. Since we’re aiming to change the world of mobile security, maybe a good place to start is to describe the security limitations on smart devices.
Like a computer, right?
Often, people think that mobile device security is exactly like PC security. Oh boy, are they wrong. There are many differences in the architecture of commonly used smart devices like Android and iOS that creates real pain to security vendors that have to stick to new rules. Unfortunately, these limitations do not stop the hackers as-well – since they do not adhere to anyone’s rules to begin with.
The products that we have developed and are releasing in 2014, as described in the first post, often made people think that we were over-shooting for trying to do the impossible. Only technical people often understood the limitations of the mobile operating environment and what was considered ‘impossible’. I will share with you why these people thought that we developed was considered ‘impossible’:
Overcoming these challenges requires out-of-the-box thinking and tireless innovation. To understand this, you have to understand the limitations and constraints that you face whilst trying to design and to provide a true Mobile IPS solution.
Security Limitations and Constraints on Smart devices
Sandbox & User Separation – Each app can only see the content of the app space provided to it, commonly referred to as a Sandbox. With user separation and the Sandbox – apps cannot interact with and investigate each other or the entire OS.
mobile se curity vendors are afforded accessibility to the APKs folder in Android, which allows them to statically ‘read’ the file and inspect if there is any malicious binaries in it (called : Signature-Based detection) – Please note that if the malicious binary is not on the APK file, and the malicious payload is only triggered by the app itself – the security vendor will not be able to access the payload and the ‘read’ attempt from the malicious app would fail (due to the sandbox – apps cannot ‘see’ each-other).
curity vendors are afforded accessibility to the APKs folder in Android, which allows them to statically ‘read’ the file and inspect if there is any malicious binaries in it (called : Signature-Based detection) – Please note that if the malicious binary is not on the APK file, and the malicious payload is only triggered by the app itself – the security vendor will not be able to access the payload and the ‘read’ attempt from the malicious app would fail (due to the sandbox – apps cannot ‘see’ each-other).
Limited API Scope – Published Security APIs are limited in scope due to the risks that may be uncovered to unwanted parties. The only API that is exposed is often tied down to Physical security actions. That’s the reason some vendors are pushing “Lock”, “Wipe” and “Find my phone” as security features.
Hooks and Global OS checks – Often a technique used by security vendors in PCs. This technique allows the inspection of the live operating system environment to detect if any malicious inputs or attempts are performed vs. a specific processes or system-calls. In phones – Apps cannot do any operating system hooks since it requires root / administrator permissions.
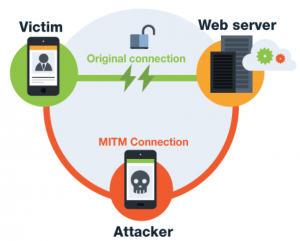
Detection of Network attacks – In a dynamic environment like smartphones – you often connect to many different Wi-Fi devices per day. To detect network attacks on PCs it requires root privileges to sniff the network packets since ADMIN_NET_CAP capability in the kernel is required to perform such task. This capability cannot be obtained while running with app permissions and therefore is ineffective at detecting network attacks on smart devices.
We worked extremely hard to re-think the entire approach. It took us 3 years, but we finally have developed a true security solution for the modern mobile age that overcomes the above constraints. We will expose more information soon on how we did this completely in user-mode and with all the above limitations and achieved:
- Endpoint detection of network attacks, including IPv4 and IPv6 scans and many types MITM attacks.
- Endpoint detection of host exploits including client-side / spear-phishing attacks.
- Endpoint detection of Kernel exploits
- Endpoint detection of Sandbox bypass techniques
- Detection of attacks outside of the sandbox.
If you are concerned about your smartphones and corporate network safety: contact us for free evaluation of zIPS our Mobile IPS which is part of Zimperium Mobile Security System.
Zuk and The Z Warriors