By:Zuk Avraham
Follow Zuk Avraham (@ihackbanme)Joshua Drake
Follow Joshua Drake (@jduck)
Last year, we disclosed a series of critical vulnerabilities within Android’s multimedia processing code — libstagefright. We promised to release the exploit for testing purposes and quickly published our exploit for CVE-2015-1538 targeting the Galaxy Nexus running Android 4.0.4. We delivered this exploit via MMS to help carriers simulate and block a potential MMS-based worm scenario. We are now ready to release our browser-based CVE-2015-3864 exploit for testing, but first let’s look at what prompted this decision.
The Impact on Android
Google responded quickly when we first notified them of the vulnerabilities we discovered. They:
- quickly accepted patches provided to AOSP
- updated the Hangouts and Messenger apps to remove automatic media processing
- started releasing monthly Nexus updates and bulletins and
- pushed OEMs and carriers to improve the way they handle and remediate vulnerabilities
Despite improvements in the ecosystem (kudos where deserved), updating Android devices remains a challenge and leaves many end users’ handsets exposed to serious vulnerabilities. Multimedia-related vulnerabilities have made an appearance in every Nexus/Android Security Bulletin to date. The most recent Android Security Bulletin in September included 11 vulnerabilities that affected Mediaserver amongst the 55 CVEs referenced. Prior to that, 460 CVEs affecting the Android platform (159 critical, 191 high, 68 moderate, and 5 with low severity) had been disclosed. Usually, an attacker needs between one and five vulnerabilities to take full control over a device. Keeping devices updated has never been more important.
Google’s Android Security Team has invested heavily in responding to media-related security problems by hardening Mediaserver (and the OS too) significantly in Android Nougat. Unfortunately, the adoption rate of new versions of Android is very slow. Nearly one year after its initial release, Android Marshmallow (6.0) is only running on 18.7% of devices in the ecosystem. If this trend continues, Android Nougat will only be used on roughly the same number of devices this time next year. Any device not updated will not benefit from a majority of the improvements Google has made in response to our (and others’) research related to multimedia processing. We implore those responsible for releasing updates to do whatever possible to rectify this situation.
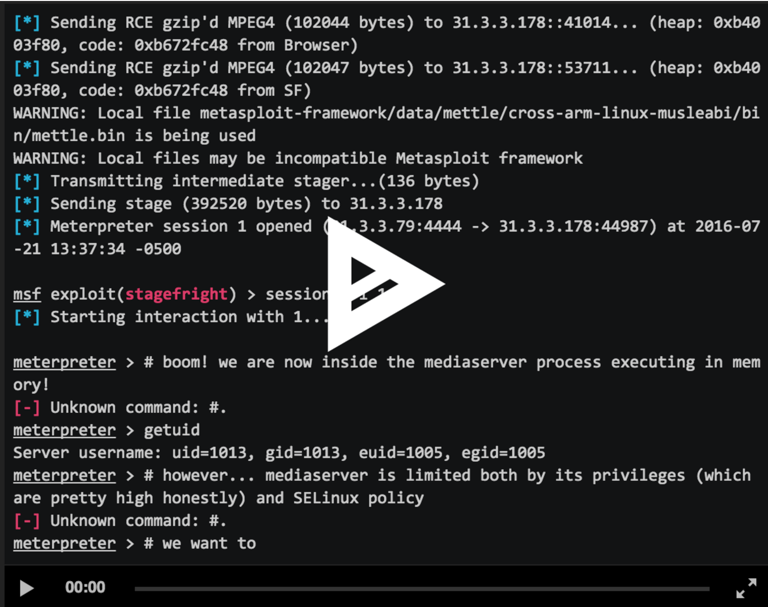
The latest effort, undertaken by our Joshua J. Drake, culminated in a Metasploit-module that exploits CVE-2015-3864 via the Web browser. This module is able to exploit a vulnerable device using only three quick HTTP requests and supports 29 different device/firmware versions simultaneously — a significant improvement over the Metaphor exploit. We collaborated with Rapid7 to integrate with the very recent “mettle” payload developed by the Metasploit team. This payload executes purely in memory, which allows operating within the SELinux policy that restricts mediaserver on Android 5.x to yield a meterpreter session.
The following builds are supported by the module at this time:
- Nexus 7 (Wi-Fi) (razor) with Android 5.0 (LRX21P)
- Nexus 7 (Wi-Fi) (razor) with Android 5.0.1 (LRX22C)
- Nexus 7 (Wi-Fi) (razor) with Android 5.0.2 (LRX22G)
- Nexus 7 (Wi-Fi) (razor) with Android 5.1 (LMY47O)
- Nexus 7 (Wi-Fi) (razor) with Android 5.1.1 (LMY47V)
- Nexus 7 (Wi-Fi) (razor) with Android 5.1.1 (LMY48G)
- Nexus 7 (Wi-Fi) (razor) with Android 5.1.1 (LMY48I)
- Nexus 7 (Mobile) (razorg) with Android 5.0.2 (LRX22G)
- Nexus 7 (Mobile) (razorg) with Android 5.1 (LMY47O)
- Nexus 7 (Mobile) (razorg) with Android 5.1.1 (LMY47V)
- Nexus 5 (hammerhead) with Android 5.0 (LRX21O)
- Nexus 5 (hammerhead) with Android 5.0.1 (LRX22C)
- Nexus 5 (hammerhead) with Android 5.1 (LMY47D)
- Nexus 5 (hammerhead) with Android 5.1 (LMY47I)
- Nexus 5 (hammerhead) with Android 5.1.1 (LMY48B)
- Nexus 5 (hammerhead) with Android 5.1.1 (LMY48I)
- Nexus 6 (shamu) with Android 5.0 (LRX21O)
- Nexus 6 (shamu) with Android 5.0.1 (LRX22C)
- Nexus 6 (shamu) with Android 5.1 (LMY47D)
- Nexus 6 (shamu) with Android 5.1 (LMY47E)
- Nexus 6 (shamu) with Android 5.1 (LMY47I)
- Nexus 6 (shamu) with Android 5.1.1 (LYZ28E)
- Nexus 6 (shamu) with Android 5.1 (LMY47M)
- Nexus 6 (shamu) with Android 5.1.1 (LMY47Z)
- Nexus 6 (shamu) with Android 5.1.1 (LVY48C)
- Nexus 6 (shamu) with Android 5.1.1 (LMY48I)
- Nexus 6 (shamu) with Android 5.1.1 (LYZ28J)
- Nexus 6 (shamu) with Android 5.1.1 (LVY48E)
- Samsung Galaxy S5 (VZW SM-G900V) with Android 5.0 (LRX21T)
New Developments
On September 7th, the day after the September Android Security Bulletin was published, Google Project Zero researcher, Mark Brand, released an analysis of and exploit for CVE 2016-3861. When we looked at Brand’s exploit, we noticed he used a nearly identical technique to what Josh used in this module. Interestingly enough, Brand found the same bug reported by Josh on August 15th, 2015. Josh’s proposed patch for this vulnerability is here. The bug report was accidentally marked as obsolete. We believe that if two independent researchers found the exact same bug, and developed the exact same techniques, the likelihood of those techniques being used for targeted attacks is high. As a result, we sped up the release of our exploit to the general public so that security teams, administrators, and penetration testers alike may test whether or not their systems remain vulnerable. We welcome the security community to build further on this work and help to maintain this module.
During our research, we identified ways that Google can make this attack less successful. We’ve already communicated these methods to Google and are happy to work with other vendors and carriers through ZHA to discuss these methods as well.
To download the CVE-2015-3864 exploit, simply update your Metasploit. If you don’t already have Metasploit, you can obtain it by following the instructions from the Metasploit developer docs.
Disclosure timeline:
- May 4th 2015: Joshua reported CVE-2015-3824 to Google’s Android Security team
- August 13th 2015: Google releases a fix for CVE-2015-3824
- August 13th 2015: Exodus discloses CVE-2015-3864 (duplicate of a Project Zero report)
- August 15th 2015: Joshua reported what eventually became CVE-2016-3861
- September 9th 2015: Google releases a fix for CVE-2015-3864
- March 24th 2016: Metaphor exploit released (showing ASLR bypass)
- May 2nd 2016: Josh’s report of CVE-2016-3861 was accidentally marked as obsolete
- June 6th, 2016: Josh shared our CVE-2015-3864 Metasploit module with the Google/Android Security Team
- August 12th 2016: Shared exploit with vendors and carriers through ZHA partners
- July 29th 2016: Shared details on the exploit with the GSMA Device Security Group
- August 9th 2016: Shared details on the exploit at WOOT in the Day 2 Keynote
- September 6th 2016: Google releases September bulletin
- September 7th 2016: Google Project Zero released Mark Brand’s exploit for CVE-2016-3861 using nearly identical techniques
- September 9th 2016: Android Security Team offered a $3,000 reward for CVE-2016-3861
- September 13th 2016: Android Security Team donates $6,000 to EB Research on Josh’s behalf (matching the $3,000 reward)
- September 23rd 2016: Public release
Zimperium customers:
Zimperium’s z9 engine detects this attack, Mark Brand’s CVE-2016-3861 exploit, and much more without requiring any update. For more information about our award winning technology, read about our products.