
As the global leader in mobile security, Zimperium is proud of the companies and governments that trust us to protect their mobile endpoints and applications. Our customers are not only well-known for their brands, they are known for being some of the most sophisticated and knowledgeable security organizations in the world.
We recently spoke with several of our Global 1000 customers across the Finance, Manufacturing, Public Sector, Telecommunications, Technology and Management Consulting industries about COVID-19 and mobile security. These organizations not only represented different industries, but also different geographies with operations in North America, Europe and Asia.
Discussion topics varied from how many of our customers’ employees are working from home now; how many anticipate working from home in the future, upticks and concerns about phishing and how overall security budgets have been impacted. I wanted to share some of their insights.
No longer the forgotten endpoint
In response to remote working and the rise in COVID-related mobile attacks, one security leader stated flatly that “mobile devices are no longer the forgotten endpoint.” As another customer noted, the overnight shift to remote working for most employees has forced organizations to acknowledge the proverbial “elephant in the living room:” mobile devices are accessing/containing corporate data and are the keys to Zero Trust/two-factor authentication (more on this point next), but most organizations have left these devices completely unprotected.
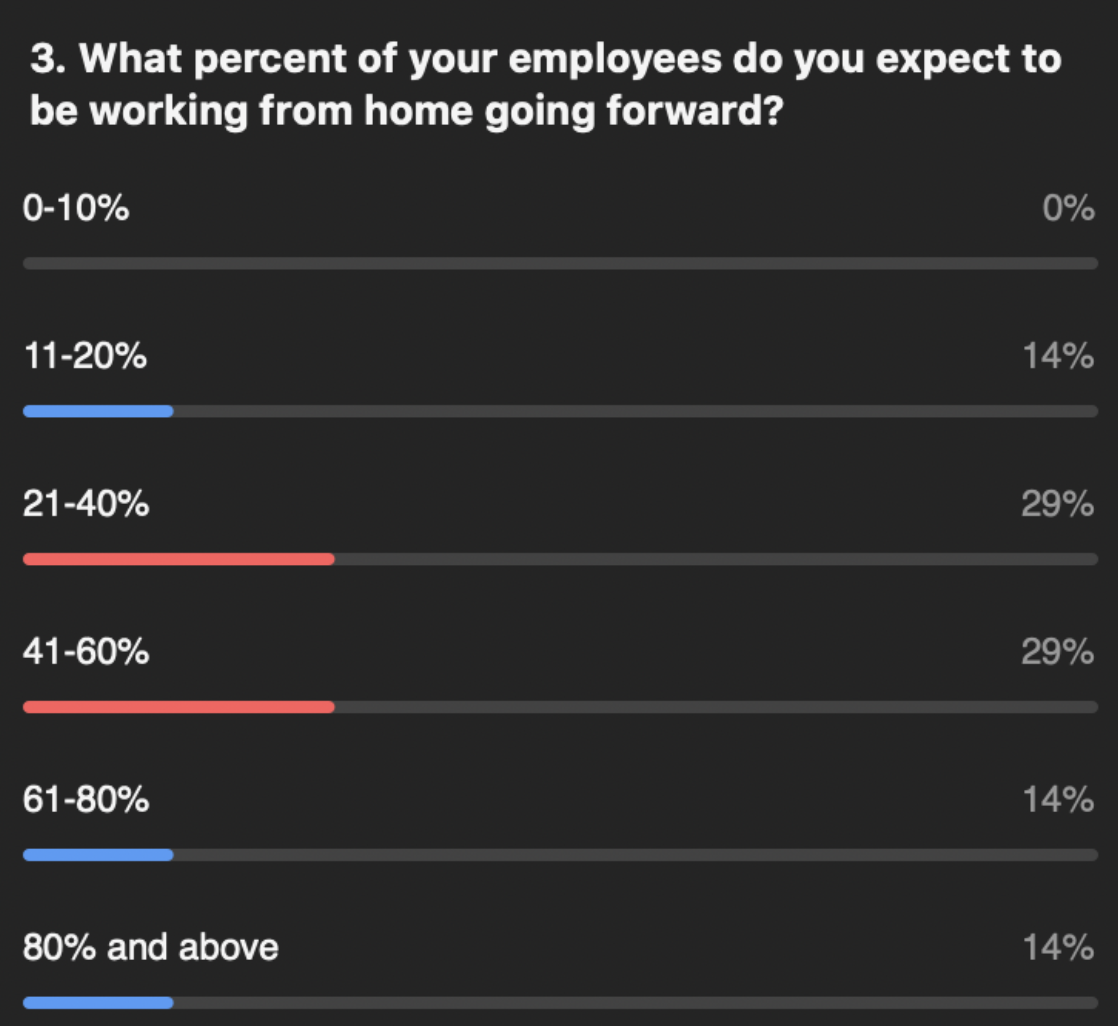
As you will see below, these leading companies and agencies fully expect remote working to be the new normal for a large percentage of their employees, so organizations simply cannot ignore mobile security anymore.
Can cripple Zero Trust/2FA
Perhaps the most important observation made by our customers was around the absolute requirement to secure mobile endpoints to protect Zero Trust and two-factor authentication (2FA) initiatives. Mobile endpoints are the Achilles’ heels for these efforts since all of their power and strength can be brought low by compromising the mobile device being used for authentication. Using 2FA as an example, the logic is brutally simple and obvious to the experts:
- Mobile endpoints are the “something you have” factor in most two-factor authentication scenarios including cloud-enabled applications being accessed by most remote workers;
- If an attacker has compromised that mobile endpoint, he can view/use (and even delete after using) the message sent for 2FA and can also view/use the password (the second factor for a complete 2FA, “something you know”) since he has complete access to the password vault.
This story is only just beginning to be told. More on it over the coming weeks.
Working from home will remain
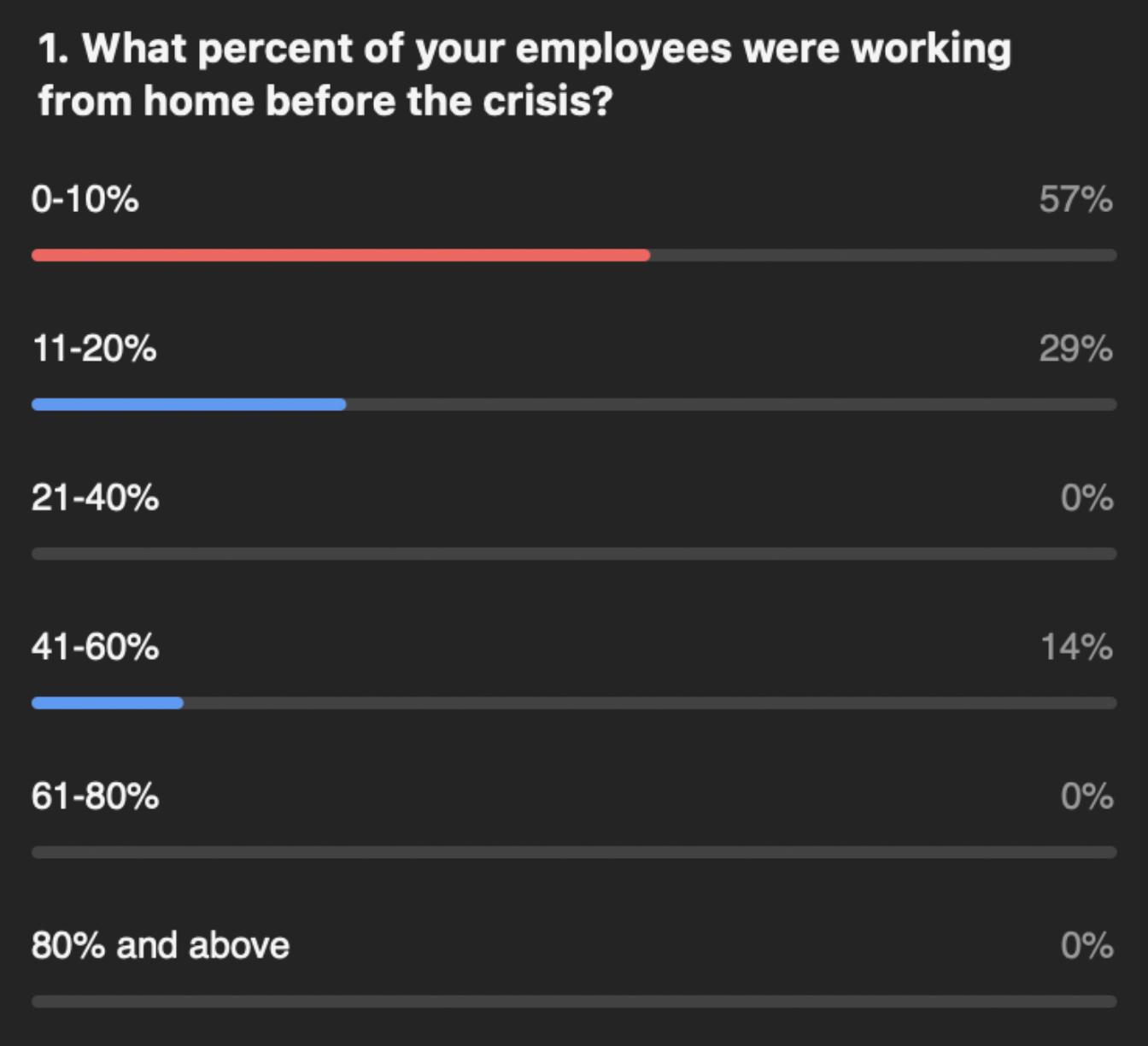
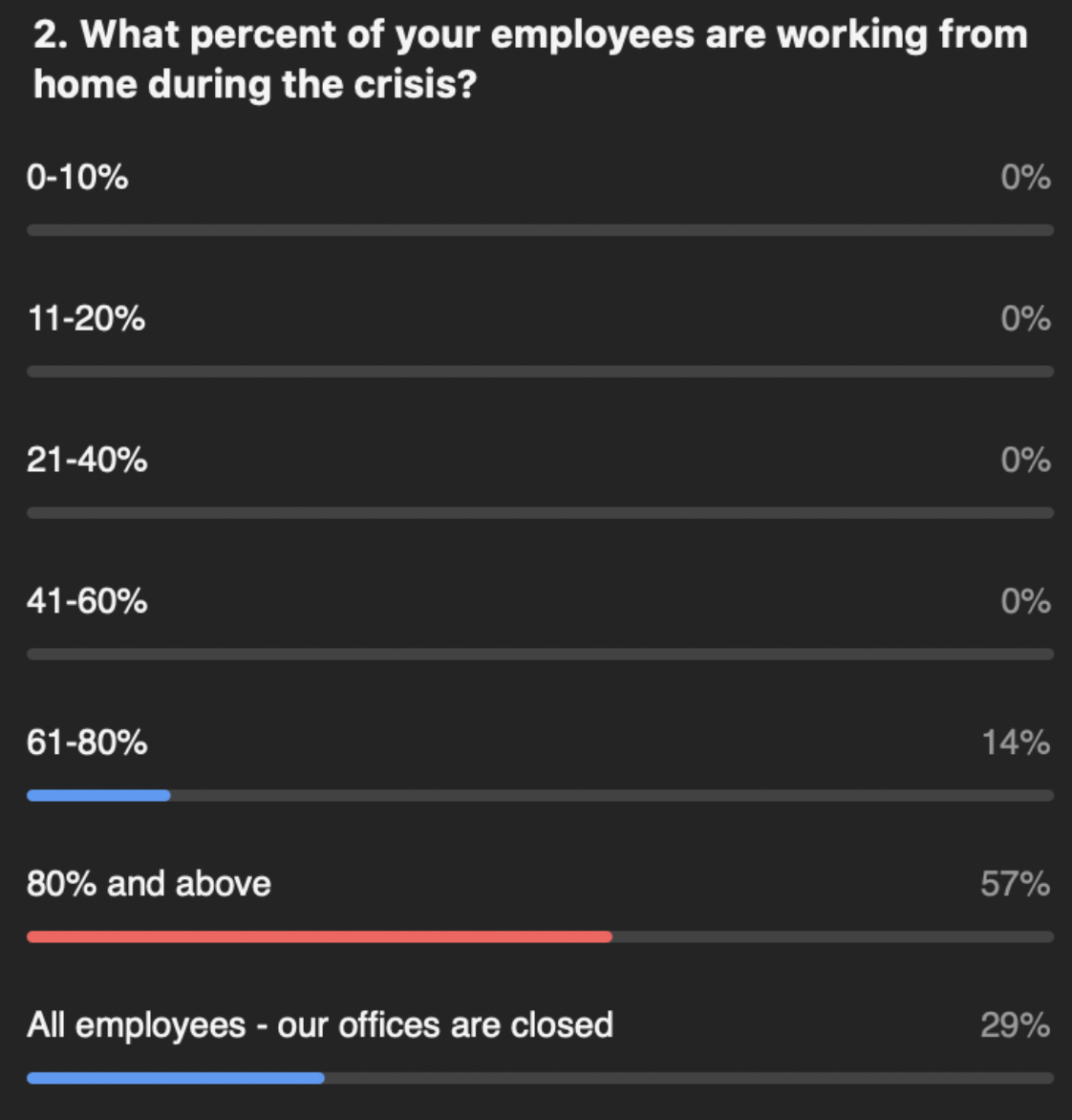
Not surprisingly, our customers reported that the percentage of employees working from home increased precipitously over the last few months. Of note though, many companies anticipate that many employees will continue working from home in the foreseeable future, even after “non-essential” employees (according to governments’ COVID definitions) are able to return to work.
Many of our customers talked about how their leadership teams were pleased with how well working from home has gone, citing increases in productivity. Lower overhead and higher productivity have created a new normal.
Phishing and malware
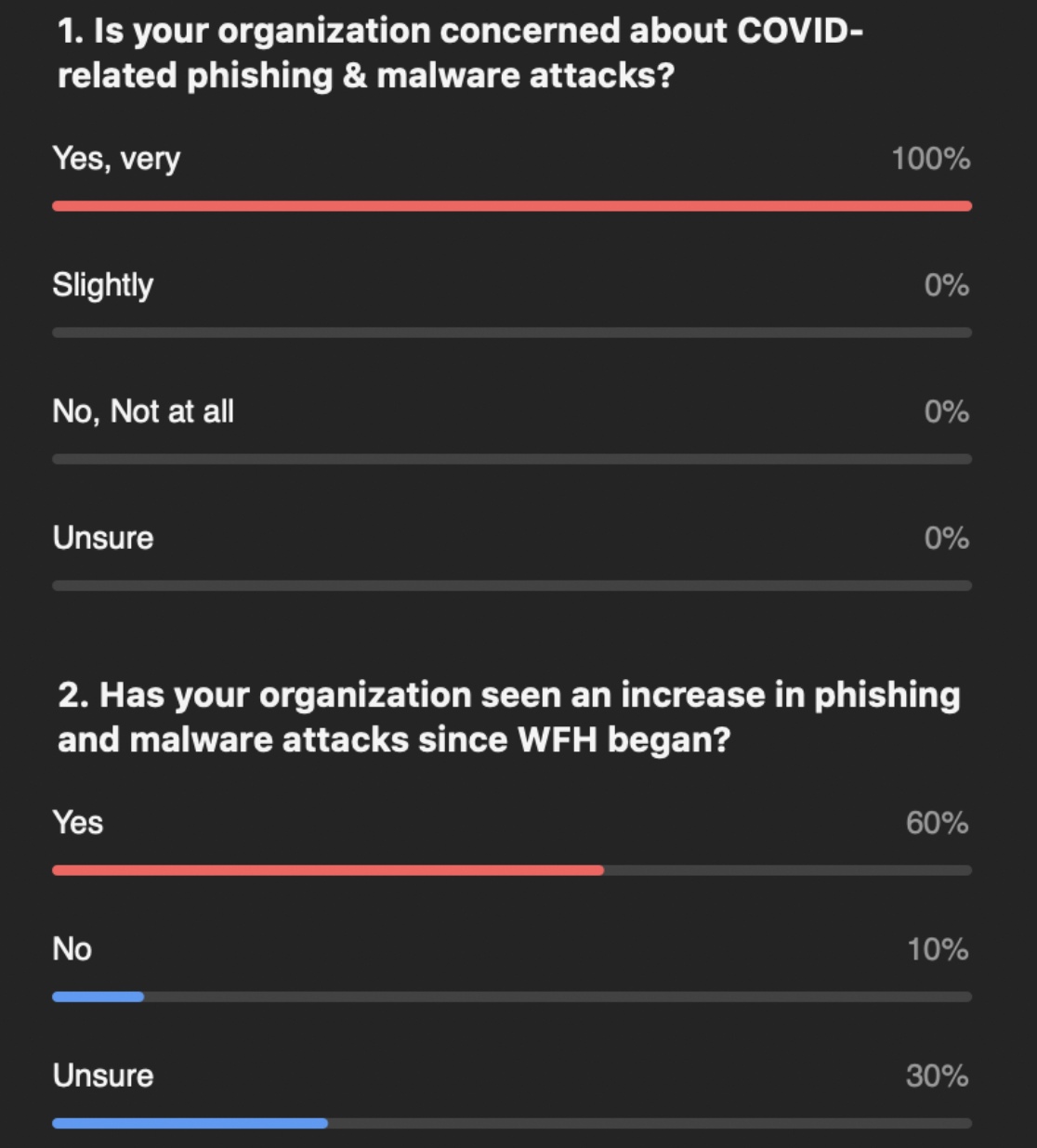
As we continue working from home during this pandemic, we’ve seen a tremendous spike in the amount of phishing and malware attacks. Our research team has identified more than 630 different phishing sites with fake COVID health and stimulus package information.
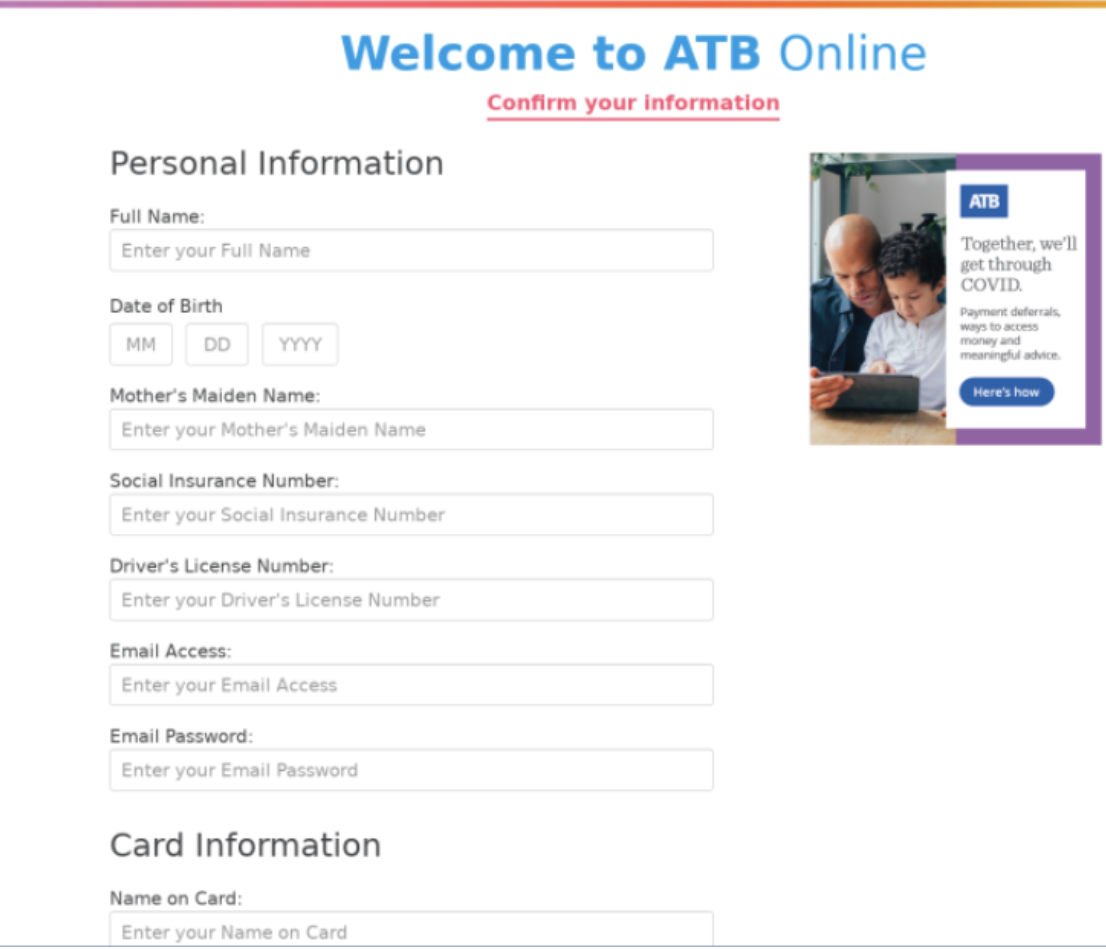
All of our customers are very concerned about these COVID-related phishing and malware attacks and a majority are aware of increases in attacks.
Poised for explosive growth
To summarize some of our customers’ key observations:
- Work from home (or work from anywhere, as some are now calling it) is here to stay;
- Mobile is no longer the forgotten endpoint and must be secured;
- Mobile endpoints can cripple the solutions experts expect to dominate the perimeter-less computing and access world going forward, Zero Trust and 2FA; and
- Mobile phishing is increasing exponentially and is a concern of all customers.
In addition to many other use cases not fully discussed in this customer session (e.g., BYOD, compliance mandates), all of these factors are creating a perfect storm that I believe will drive explosive growth for enterprise mobile security over the next few years.
Zimperium Can Help
If you would like to learn how to reduce your risk from mobile threats and enable secure remote working environments, Zimperium is here to help you. Please contact us by clicking here.



