Over the last few months, the Zimperium zLabs team has been actively monitoring the rise in phishing attacks and some new data started to stand out. While phishing has predominantly been device-agnostic, meaning it did not rely on or change based on the operating system or device type, a trend began to emerge showing an increase in mobile-specific phishing websites.
Crafting a phishing attack gets easier every day with tools and phishing kits that allow even novice users to deploy deceptive sites using just a few clicks. But detecting these attacks has not improved for many security services and the number of attacks keeps increasing over time.
While there are different types of phishing attacks, the Zimperium zLabs team has been monitoring the rise in deceptive phishing specifically targeting mobile endpoints.
A deceptive phishing attack is the product of attackers crafting websites mimicking well-established brands and finding ways to direct users to them. When a user submits their credentials to the compromised site, the attacker is able to take control of the victim’s account. Amplifying the severity of these types of attacks and the spread of compromise are user’s tendency to reuse passwords across many accounts. Essentially, one password could be the key to the full data kingdom.
As remote and distributed workforces have become the norm for many enterprises, it is the apparent corporate infrastructure is still trying to catch up to the new normal. Unfortunately, this has left employees without the protective layers that exist within office spaces, leaving corporate data at risk to attack. And this new norm has also introduced the mobile device as a highly critical component to the average employee’s workflow. But the smaller screens of these endpoints are an advantage to attackers; the critical data needed for a user to detect if a link or website is phishing is often hidden from view, making the weakest link even more vulnerable.
This has become the biggest incentive for malicious actors to specifically target mobile.
The Rise of Mobile-Specific Phishing
Relying on legacy security tools to detect these advanced phishing threats on mobile devices presents bigger challenges compared with any other environment. The commonly relied on sandboxing toolsets do not deliver the critical information necessary for advanced detection, and processors often limit the capability of analysis for each visited domain. The difficulty for users installing and adopting browser extensions increases the lack of information any security solution has available. In most cases, it is not possible to install browser extensions on mobile browsers. There are some exceptions (recently Safari and Firefox announced this feature), but the procedure is not as simple as in a desktop browser and/or the extension catalog is reduced for mobile. Using a browser extension, the phishing analysis tool has visibility of website content as html, links to external resources, full url, etc. Knowing this, as a general rule, phishing analysis tools on desktop work with more information than phishing analysis on mobile.
Attackers are well aware of this and are focusing their efforts on mobile-specific phishing attacks. They are using two different strategies — adaptive and responsive websites — to generate mobile-specific content.
Adaptive Websites
Adaptive sites load completely different content according to the device accessing the page. This is achieved by checking the user agent of the mobile endpoint and allows the developer to display specific content only for specific devices. This is also an easy way for malicious websites to avoid detection through legacy desktop traffic or phishing analyzers.
The desktop site redirects to a decoy site (three.co.uk) while on mobile the victims would see a phishing site mimicking Netflix.
The first two examples are returning a 404 not found error when the site is accessed through a desktop user agent but display as a valid phishing site when accessed through a mobile device.
The third example is the most interesting of this series since a user will get a valid site independent of the user agent, but will be redirected to a phishing site targeting Netflix only if the website is accessed through an Android mobile device. Any other device, including iOS, will be redirected to another legit decoy site otherwise. While this technique was seen in the past with different redirections based on the mobile OS, it is a strong indicator of some browser vulnerability being exploited. This is the same technique used by the Pegasus spyware through the validation servers, preventing security researchers from exposing NSO infrastructure.
Responsive Websites
Responsive websites adjust the distribution and size of the objects to the screen size of the endpoint connecting in. While the same content is displayed, it will appear in different sizes and positions according to the size of the device’s screen. Most modern web development frameworks generate responsive content for a cohesive web experience across all endpoints. But this framework also gives attackers an edge when it comes to phishing.
As an example of these types of sites, the images below show the difference of loading the Paypal.com site from mobile and desktop.
The next screenshot shows a responsive phishing site targeting Chase, loaded on desktop and on a mobile device.
The Scope of Mobile-Specific Phishing Attacks
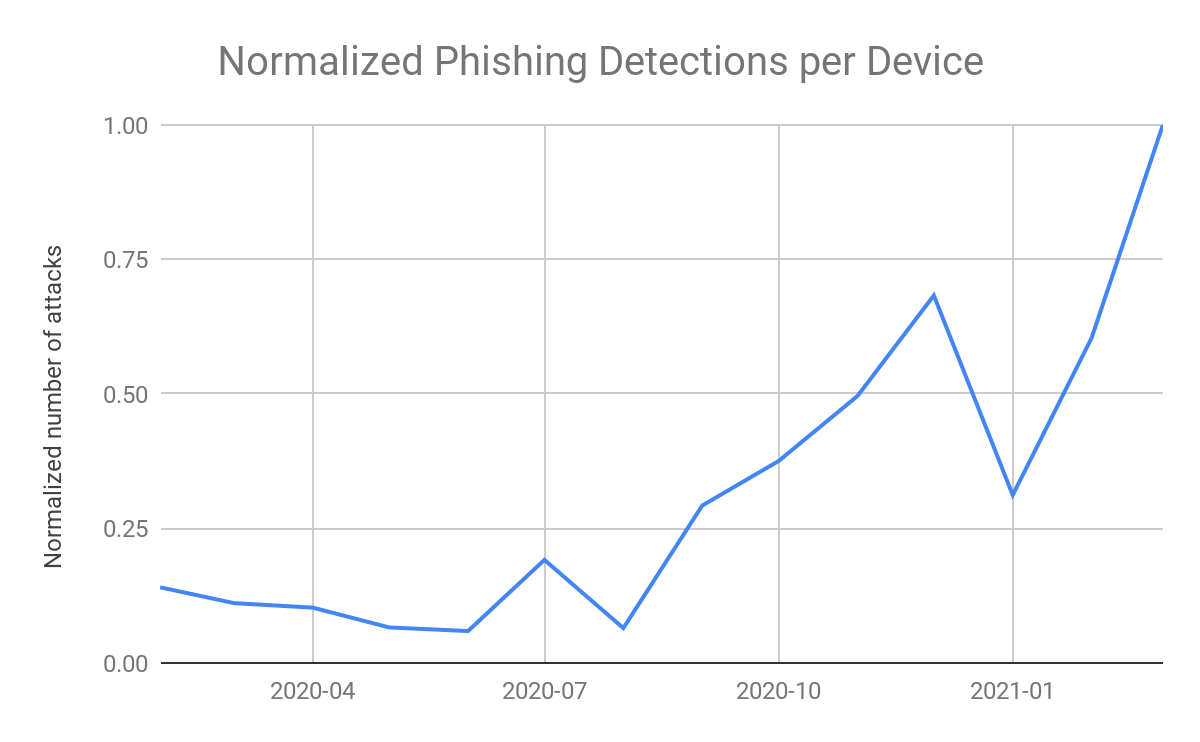
During the last few months, Zimperium’s internal dataset has shown an increase in the number of phishing attacks around the world. As Zimperium is a mobile security provider, we correlate the detected data with an increase in phishing attacks targeting mobile. But to better understand and verify the theory of a trend in mobile-specific phishing, we turned to outside data for analyzation.
We conducted an analysis for the data from both publicly available and private data sources during a period of two and a half years and checked for responsive and adaptive sites. In that period of time, 500K phishing sites were analyzed. As part of the research, we removed phishing data sourced from our own threat intel in order to avoid biasing the results.
We plotted the percentage of phishing sites that are able to exploit mobile month over month, revealing the upward trend in mobile-specific phishing websites. The analyzed data of third party data shows more than 50% increase in mobile-specific phishing websites in the analyzed period.
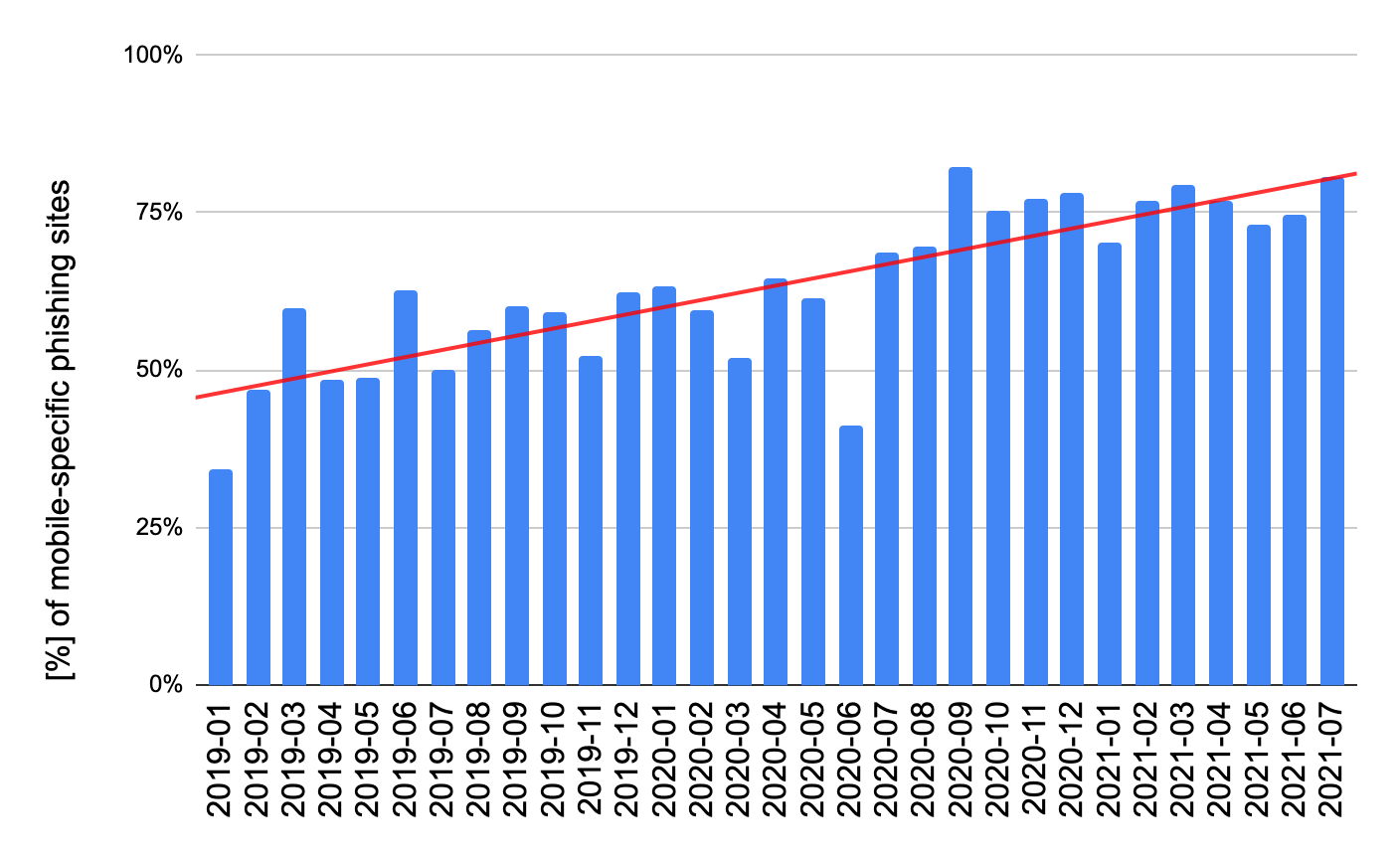
Looking at the data together, the picture has become increasingly clear as 75% of the phishing sites analyzed adapt to mobile devices through one of the two mentioned techniques. Malicious parties are specifically targeting mobile devices with phishing attacks, taking advantage of the rise in popularity and usage as well as the nuances in their use. And with great success when going up against legacy anti-phishing tools and security layers.
Mobile Phishing Through Applications
We would be remiss if we did not talk about the use of compromised and malicious applications for phishing. Commonly found on third-party app stores targeting iOS and Android devices, these malicious applications use deception and clever language to manipulate victims into installing these apps onto their mobile devices. Once installed, the user will often fall for the same scams found on these mobile phishing sites, compromising their data and credentials to cybercriminals.
Recently, Zimperium’s zLabs team discovered a malware campaign codenamed FlyTrap. While these apps seem to be legitimate, they ended up stealing Facebook credentials and session cookies to take control of the victim’s social media accounts.
Phishing Security is Critical Security
Phishing detection is difficult and there are no one-size-fits-all solutions. Most legacy systems rely only on crowdsourced lists and basic sandbox technology. While these approaches provided decent N-day coverage, most phishing sites are only alive for a few days. And these legacy layers do nothing to protect against zero-days phishing attacks.
Zero-day protection is critical for organizations. A blocklist-based approach is likely to protect against broad target campaigns, but if an organization is targeted directly in a spear-phishing campaign, the sites used won’t be on any publicly available blocklist.
It is no secret that traditional desktop endpoints have an edge over mobile systems since they do not have strong restrictions around processing power. And while browser extensions, which have the best opportunity to catch phishing sites, are widely used on desktop, they are not common among mobile users, preventing the adoption of these security layers. Attackers know this and are adapting to target mobile users.
Most legacy mobile phishing solutions use cloud services to classify sites as malicious or legitimate. While effective, there is still a delay in the determination, presenting an opportunity for an attacker due to the limited amount of processing that can be done on each site. These lookup layers have also proven to be trivial to bypass by a malicious actor on the network.
At Zimperium we approach phishing with an advanced, defense-in-depth mindset. Our machine learning powered solution provides on-device security, capable of zero day detection even when the device is not connected to a network. This machine-learning layer is complemented by standard detection mechanisms, leveraging the extensive intelligence created by the community to detect phishing N-days. And finally, the phishing security solution has a cloud-based layer allowing further analysis of potentially malicious websites.
Zimperium’s ML classifiers use different approaches to classify individual sites to prevent evasion techniques from rendering the classification useless. So even when websites are heavily obfuscated, they can still be processed. At the same time, state of the art on device malware classifiers are used to prevent malicious applications from exploiting app based phishing.
About Zimperium
Zimperium, the global leader in mobile security, offers the only real-time, on-device, machine learning-based protection against Android, iOS, and Chromebook threats. Powered by z9, Zimperium provides protection against the device, network, phishing, and malicious app attacks. For more information or to schedule a demo, contact us today.