
Enterprises are continuing to work remotely and use BYO mobile devices. Doing so enables cost savings from a corporate standpoint and better user satisfaction from an employee standpoint. It also introduces and keeps Microsoft’s O365 as a mainstay.
I recently hosted a webinar with our very own Kern Smith, Vice President of Solution Engineering, on the top four threats facing O365 on mobile devices and what can be done to stop them.
To watch our on-demand webinar, please click here. To learn more about how we are protecting devices with O365, please contact us.
Why protect mobile devices
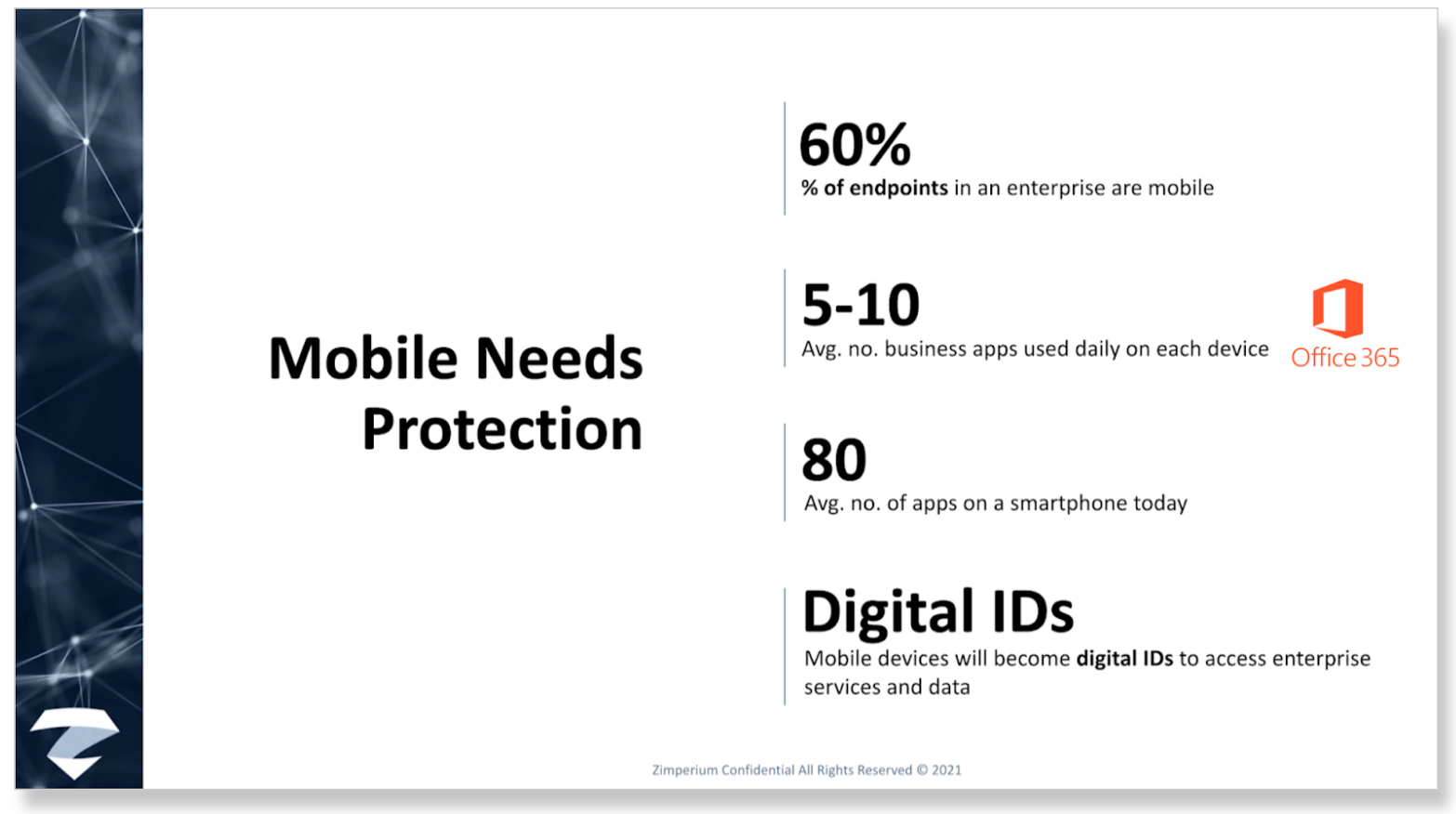
The majority of endpoints accessing the enterprise today are mobile and they have almost no protection on them. These mobile devices are spending all this time outside of the protected corporate network. The mobile devices are in the hands of users who are the ones who are usually making the worst decisions.
And why should we care if our employees make a bad decision or fall victim to an attack?
Well, it’s all of the data and information that’s accessible on and from your mobile device. For example, the typical mobile device has – on average – 80 apps on it; five to 10 of which are business-related apps, including O365 apps like Outlook and Teams. And that’s growing, especially in the remote working/zero trust world – – as is using mobile devices as a multi-authentication tool to access enterprise services and data.
4 threats to O365
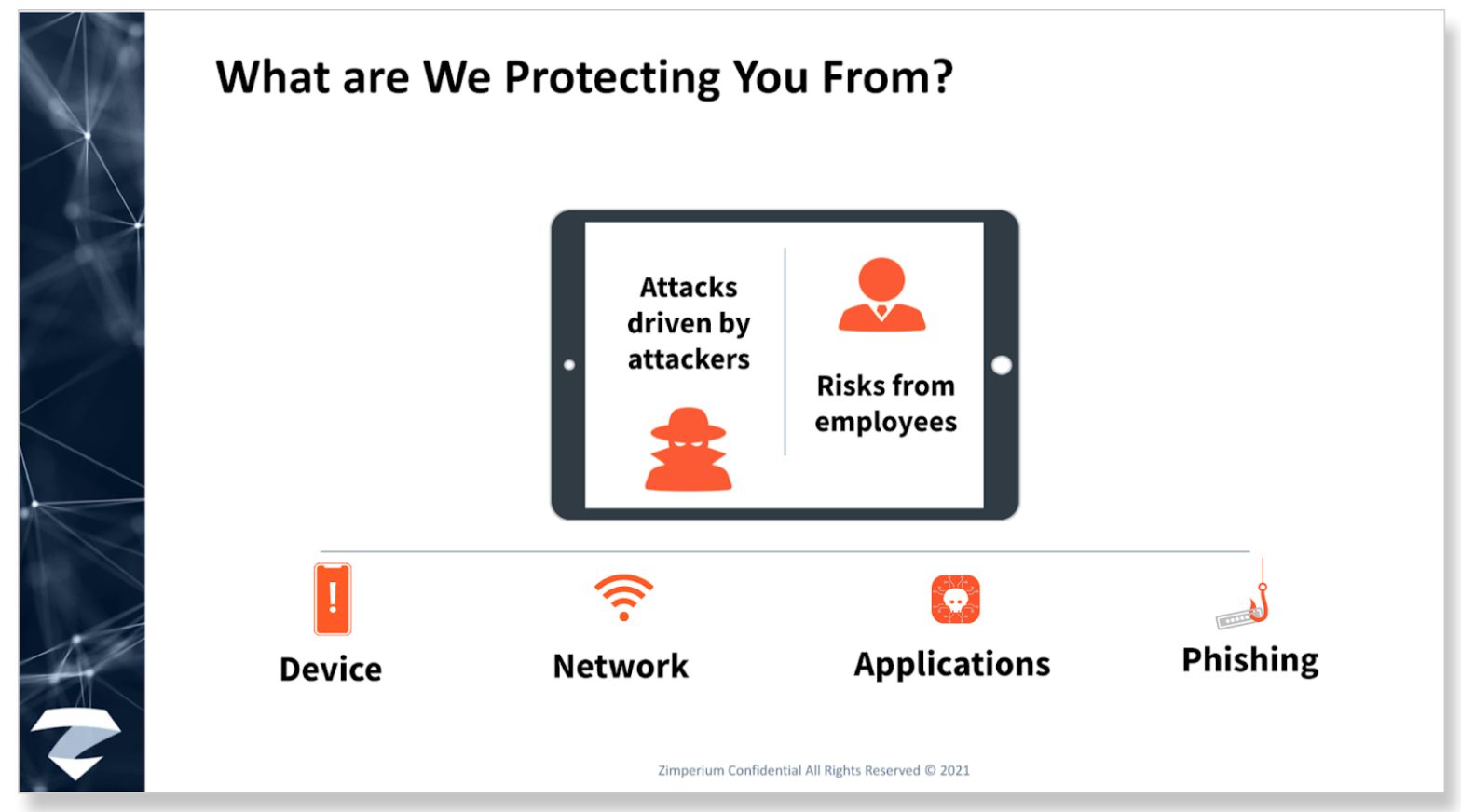
While there are – indeed – four threats to O365, there is one big risk we mentioned before, which bears repeating. The carbon-based life forms known as your employees. To be clear, it isn’t all of your employees. This is Darwinism at its finest and the bad guys are looking for the weakest link.
You see, it just needs to be one employee who doesn’t update the OS because it’s going to mess up the battery life or slow down the speed of Candy Crush. What ends up happening is the window is left open and it makes it that much easier for the attackers to….well, attack.
The end game for an attacker is to elevate privileges and compromise the device. There are three other conduits or pipelines the bad guys use in order to get to that ultimate goal of device persistence – – network, malicious app, and phishing attacks.
One of the dumbest things about smart devices is they connect to the network by introducing themselves, not the other way around. Your phone literally walks up to every network and asks, “Hey, are you Starbucks?” And the bad guys, posing as the network can easily say, “well, yes I am.”
While the majority of the malicious apps we see are actually focused on fraud – BankBot, BlackRock and the like – malicious apps can also be a delivery mechanism to compromise the device.
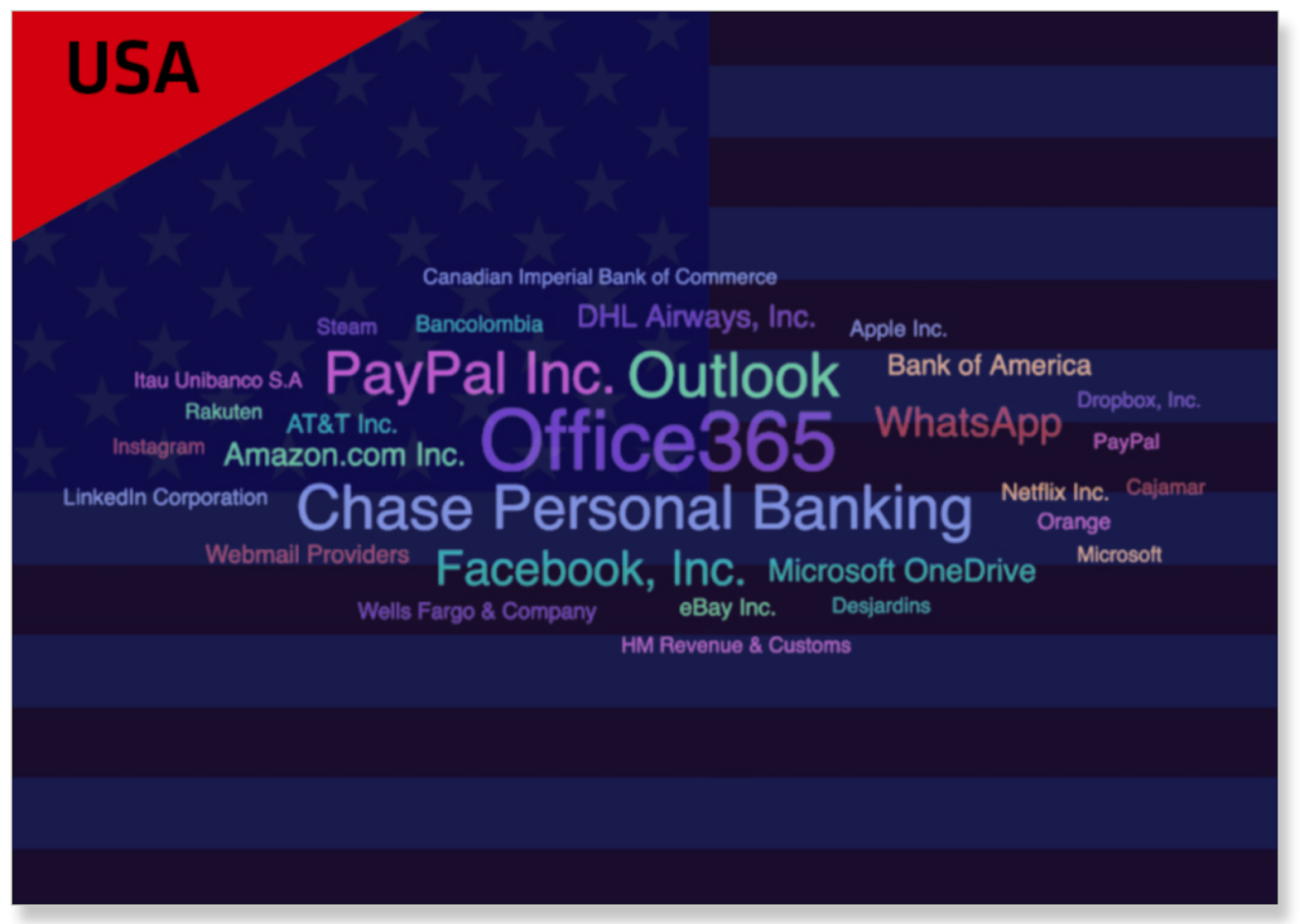
From a phishing standpoint, overall we saw a 6X increase in 2020. In the United States, Office 365 and Outlook were two of the most often used brand names attackers leveraged in phishing attacks:
Microsoft is ahead of the curve
As shown, giving mobile devices the ability to access corporate resources is creating cybersecurity threats. Microsoft, following a Zero Trust strategy, understood the threats and looked toward mobile threat defense (MTD) solutions for device attestation. The MTD provides intelligence within their conditional access approach.
For example, before allowing access to Outlook or Teams, the MTD – working with Microsoft’s Conditional Access – will alert the enterprise if the user has downloaded a malicious app. This allows the enterprise to deny access to its Office 365 solution until the app is removed.
In our webinar, we specifically showed how Zimperium’s zIPS is being used to protect Office 365 users around the world every day. zIPS is the only mobile security solution with on-device, machine learning-based detection of device, network, phishing, and malicious app attacks.
Deploying and remediation could not be easier. Here, Kern shows just how easy:
For more information
To watch our on-demand webinar, please click here. To learn more about how we are protecting devices with O365, please contact us.



