Earlier this week, Zimperium (@ZIMPERIUM), the leader in mobile threat protection, unveiled a major vulnerability in Android – Stagefright. Joshua Drake (@jduck), VP of Platform Research and Exploitation and a senior member of Zimperium zLabs, proactively studied the code. According to a few firms, other people have identified vulnerabilities in Stagefright which lead us to believe that this vulnerability and others are actively being exploited in the wild.
Zimperium Mobile Threat Protection customers are safe from this threat, even without updating the device to the latest Android version. If you are concerned that your organization is under MMS attacks – contact us here.
Question: What ability or privileges does this vulnerability provide the attacker?
it is estimated that 50 percent of the affected devices would be able to trigger the vulnerability without any user interaction. For other cases, simply opening the MMS will compromise the device.
During successful attacks, the attacker is able to run arbitrary code on the target device with media or system privileges the audio and camera of the device. Using these privileges, an attacker can perform reconnaissance on their victim by listening in on conversations, and enabling video recording.
On some devices, the affected software runs with “system” privileges. On these devices, the attacker has significantly elevated privileges. On these devices, the attacker has almost full control of the device already.
Apart from these elevated privileges, remote code execution allows sophisticated attackers to execute “privilege escalation” attacks, which allow the attacker to change “roles” on the device – providing unfettered control: access to read the victim’s emails, facebook/whatsapp messages and contacts, access data from other applications or use the device as a pivot into the customers network and cloud applications.
The attacker can hide traces of the attack by simply deleting the infected message after a successful attack. If an attacker spends additional time refining the attack, it can be made silent. In a less sophisticated attack, the victim would see one or more MMS notifications.For failed attack attempts leftover of strange MMS would appear on the device.
Question: How to protect from Stagefright?
We have received a huge volume of request from enterprises asking how to protect from this risk. We are releasing general guidelines that organizations can implement to minimize any exposure to Stagefright.
The Stagefright vulnerability was assigned with the following CVEs:
- CVE-2015-1538
- CVE-2015-1539
- CVE-2015-3824
- CVE-2015-3826
- CVE-2015-3827
- CVE-2015-3828
- CVE-2015-3829
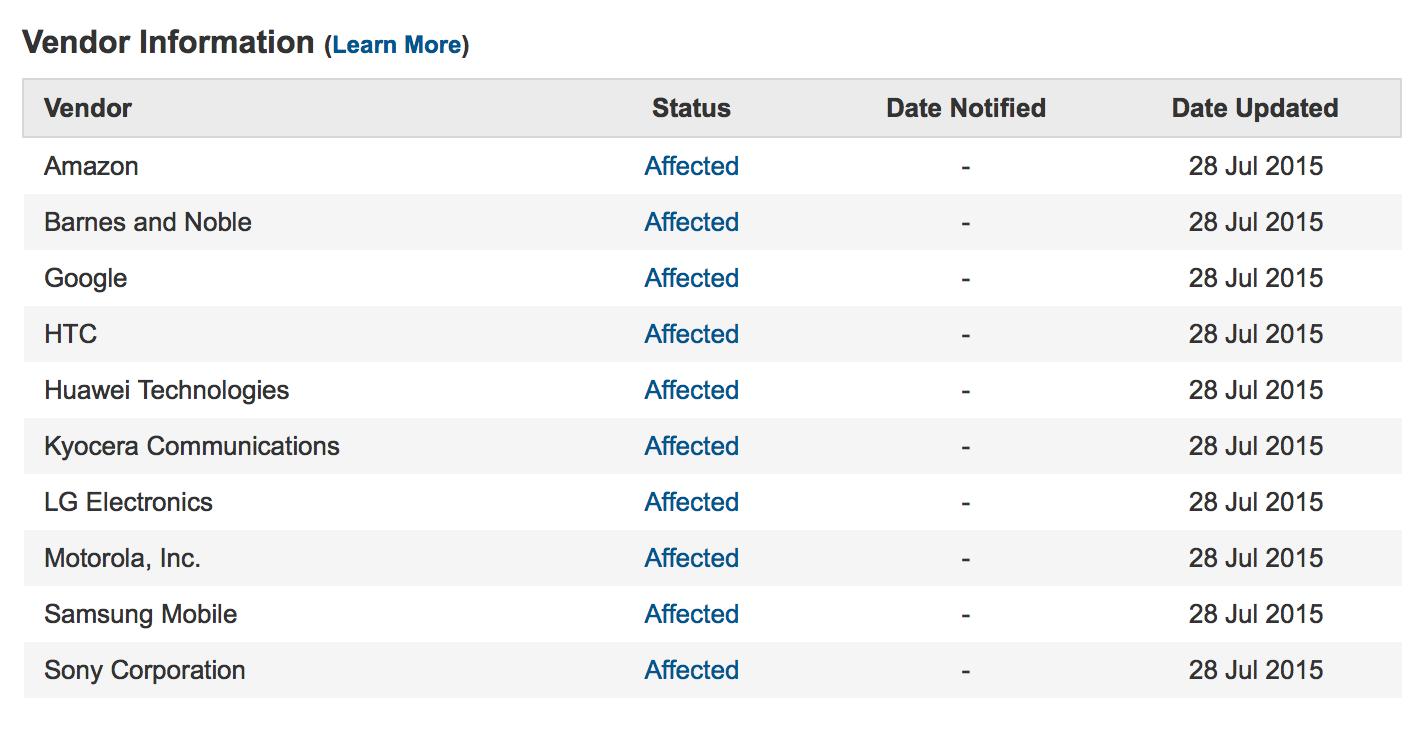
The following devices are affected:
Protection
- Update your device: Keep your device updated to the latest version at all times. If an update is not available for your device, manually install an OS like CyanogenMod that support older devices for a longer period of time.
- Disable Auto-fetching of MMS: You will need to disable this for both Hangout and regular messaging apps. Here’s how:
- HANGOUT: DISABLE AUTO FETCHING MMS
- Open Hangout
- Tap Options on the top left corner

- Tap Settings -> SMS
- In General, If you have Hangout SMS Enabled then in the Advanced uncheck Auto Retrieve MMS

- MESSAGES: DISABLE AUTO FETCHING MMS
- Open Messages
- Tap More -> Settings -> More Settings

- Tap Multimedia Messages -> Turn OFF Auto Retrieve.

Advanced Protection
Zimperium’s advanced mobile threat protection solution – zIPS, is already trained by our core engine z9, to detect and protect from Stagefright. Devices with zIPS activated are fully protected without the need for device update or disabling the MMS.
If you would like to protect your enterprise from any Stagefright threat, or learn more about Zimperium solutions, connect with our team.
Zimperium not only notified Google of this vulnerability, but also provided patches which were implemented within 48 hours. With in-depth understanding of this risk, we will continue to update you on this issue. Stay in touch with Zimperium through our blog or twitter: @ZIMPERIUM.
UPDATE:
- Zimperium’s Mobile Threat Protection customers are safe from this threat, even without updating the device to the latest Android version. Companies that have reasons to believe that they are under active Stagefright attacks, should contact us ASAP at stagefright-urgent@zimperium.com
- Zimperium Research Labs (zLABS) will release a video later this week with a Stagefright RCE demonstration. Several large carriers requested that we delay the release of our working exploit. We agreed, given the gravity of the situation. Unfortunately, because the patches are open-source [1, 2], many researchers are already working on creating an exploit. We are planning to release our exploit on August 24th, 2015. However, if an exploit is publicly released or attacks are detected in the wild before that date, we will release ours for testing purposes at that time.
- Device vendors receive the patches months after they are released. To solve this issue, ZIMPERIUM provides a global platform to assist smartphone vendors and Carriers who wish to receive mobile OS patches from Zimperium directly. Join the Zimperium Handset Alliance through – https://groups.google.com/d/forum/zimperium-handset-alliances (use your vendor/telco email to be accepted to ZHA. Other requests will get automatically rejected). More than 17 of the largest vendors and carriers have already joined ZHA.
- You can read how to disable auto-fetching MMS on Nexus devices here
- ZHA partners already received proof-of-concept code that triggers the issues and the full set of Stagefright patches. For carrier specific tips – check this post
- Josh will present the full details of his research at Black Hat on August 5th or DEFCON on August 7th. We invite you to join us!

